Zero Trust in the Cloud: Building Security for a Borderless World



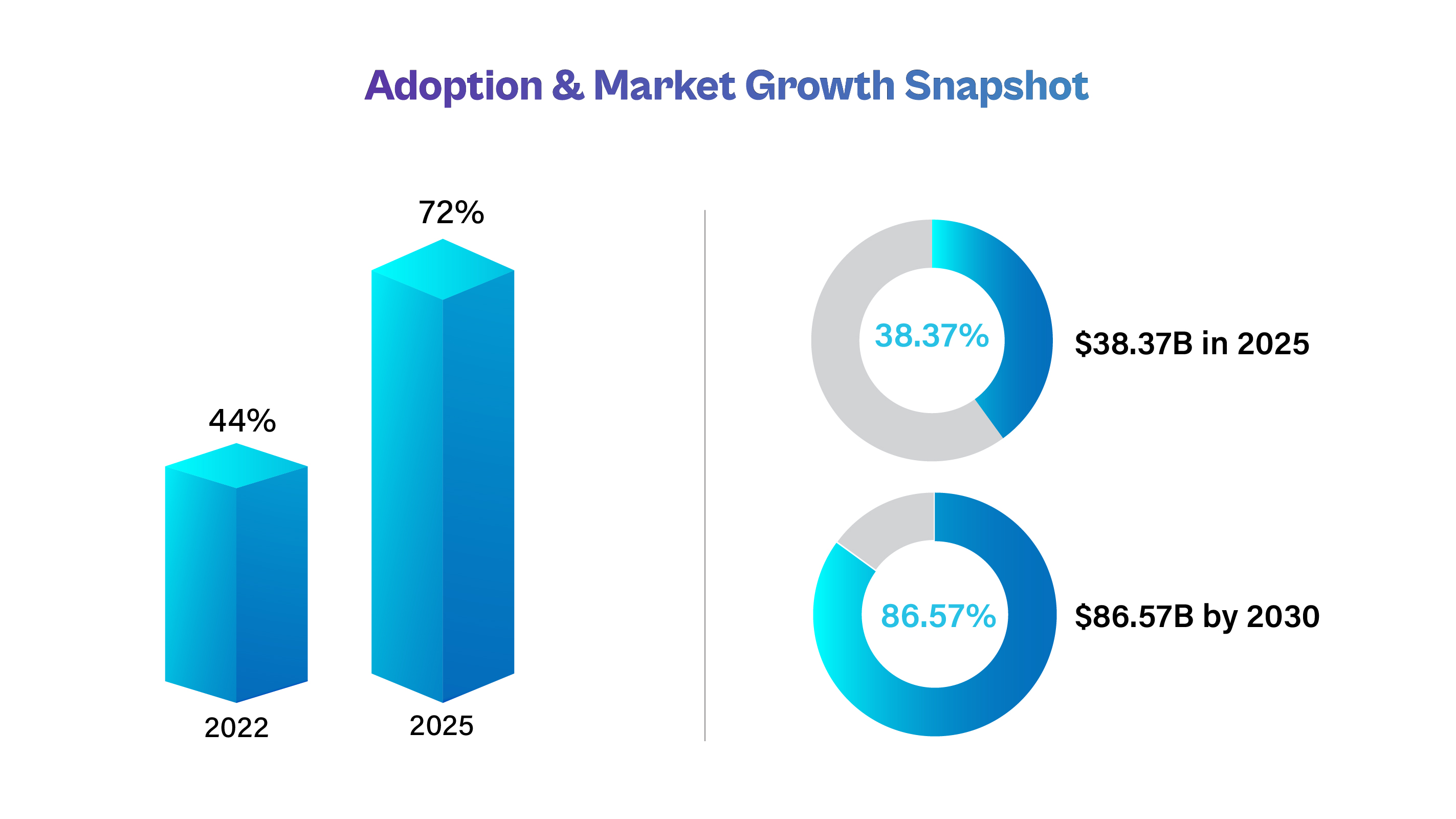
The shift to a Zero Trust approach is radically reshaping cloud security, driven by the soaring complexity of hybrid work and digital transformation. According to the 2025 Cybersecurity Adoption Index, 72% of global enterprises have adopted or are actively implementing Zero Trust frameworks, up from just 44% in 2022. This represents a 30% surge over the past three years. This rapid momentum is mirrored by an expanding market, which is now at $38.37 billion and is projected to grow to $86.57 billion by 2030. A remarkable 63% of organizations specifically cite cloud security as the primary driver for adopting Zero Trust, and those that have implemented it report, on average, a 50% faster threat detection and response time, as well as a 42% reduction in security incidents.
But what makes Zero Trust so pivotal? Unlike legacy perimeter-based approaches, which assumed trust within internal networks, Zero Trust treats all interactions, both inside and outside the organization’s boundaries, as potential threats. In the age of the cloud and remote work, where rigid boundaries no longer exist, Zero Trust mandates "never trust, always verify": every user, device, and application must continuously prove their legitimacy through strict authentication, adaptive controls, and real-time monitoring. This relentless scrutiny has become essential as surging cloud adoption, mobile access, and third-party integrations expand potential attack surfaces.
Evolution of Zero Trust Beyond the Perimeter
.jpg)
For decades, enterprise security was built on the assumption that everything inside the network perimeter could be trusted, and everything outside it posed a threat. Firewalls, intrusion detection systems, and VPNs were designed to reinforce this castle-and-moat model. But in the era of cloud-first strategies, mobile workforces, and SaaS ecosystems, the concept of a well-defined perimeter has become obsolete. Attackers now exploit stolen credentials, misconfigured APIs, and insider access with alarming ease, bypassing traditional defenses. This shift in threat dynamics gave rise to Zero Trust, not as a single product but as a philosophy of continuous validation.
The first wave of Zero Trust adoption focused on extending the perimeter inward, securing corporate networks by enforcing identity and device authentication at access points. Google’s BeyondCorp initiative in the early 2010s marked a turning point, demonstrating that employees could securely access corporate resources without a VPN if their identity, device health, and context were verified at every request. Around the same time, the Jericho Forum and early NIST publications began codifying the principle that trust should never be implicit.
The second wave came with the formalization of NIST SP 800-207, which defined Zero Trust Architecture (ZTA) as an end-to-end framework. This framework moved beyond network boundaries and emphasized policy enforcement points (PEPs) and policy decision points (PDPs) that continuously evaluate access requests against identity, device, and behavioral signals. In this stage, Zero Trust was increasingly tied to identity and access management (IAM), privileged access controls, and micro-segmentation of workloads.
Today, we are entering the third wave of Zero Trust, which extends beyond the perimeter, network, and into workloads, applications, and data. Modern Zero Trust models are:
- Identity-Driven: Every entity, including humans, devices, workloads, and APIs, is authenticated with adaptive, risk-based controls.
- Context-Aware: Policies adjust dynamically based on user behavior, device posture, location, and workload sensitivity.
- Workload-Centric: Security travels with the application or function, regardless of whether it runs on-premises, in a VM, in Kubernetes, or in a serverless function.
- Analytics-Powered: Continuous monitoring and AI-driven anomaly detection provide visibility into lateral movement, insider threats, and advanced persistent threats (APTs).
Zero Trust has evolved from a network initiative into a business-wide strategy that supports DevOps, compliance, and user experience. Rather than hindering innovation, it enables secure adoption of multi-cloud, hybrid, and distributed models. As the traditional perimeter disappears, Zero Trust is becoming the default security posture, embedded directly into cloud platforms, SaaS, and identity services. Its future lies in deep integration and automation, reflecting the shift from defending boundaries to enforcing trust continuously across all interactions.
Protecting Workloads in Multi-Cloud and Hybrid Ecosystems
Enterprises are no longer bound to a single platform. Modern digital strategies often rely on a multi-cloud approach that spans AWS, Microsoft Azure, Google Cloud, and specialized SaaS providers, while retaining some critical workloads on-premises in hybrid architectures. This model offers agility, cost optimization, and best-of-breed services. But it also creates a fragmented security landscape where policies, controls, and visibility vary from one environment to another. Attackers exploit these inconsistencies: a misconfigured storage bucket in one cloud, an unpatched virtual machine in another, or an overlooked IAM role in a private datacenter can become the entry point for a breach.
This complexity makes Zero Trust Architecture (ZTA) not only beneficial but also essential in multi-cloud and hybrid ecosystems. Zero Trust provides a unifying security model that enforces consistent policies across all environments, irrespective of where workloads reside. Organizations transitioning to multi-cloud and hybrid environments face fragmented controls, data mobility risks, and an expanding attack surface. The table below maps these challenges to practical Zero Trust solutions, with example tools and the strategic outcomes they deliver.
Securing Serverless Computing with Zero Trust
Serverless computing is now central to cloud-native strategies, with platforms like AWS Lambda, Azure Functions, and Google Cloud Functions enabling rapid innovation at scale. Yet the ephemeral, event-driven nature of serverless workloads introduces risks that traditional perimeter and agent-based security can’t contain.
Zero Trust provides a modern framework by embedding verification and least privilege into every serverless interaction. For leaders, the model can be understood across three strategic pillars:
Pillar 1: Identity and Access Integrity
What it means: Every function is treated as a unique identity with its own short-lived credentials, eliminating hard-coded secrets and static keys. Least-privilege and context-aware access ensure functions do only what they’re designed for.
How it’s done:
- Federated Identity & Tokens: AWS STS, Azure Managed Identities
- Fine-Grained Access Controls: AWS IAM ABAC, Okta, Azure AD Conditional Access
- Just-in-Time Secrets: HashiCorp Vault, AWS Secrets Manager
Leadership takeaway: Prevents the kind of IAM over-permissioning seen in the 2019 Capital One breach, where a single misconfigured role exposed millions of records.
Pillar 2: Continuous Monitoring and Runtime Security
What it means: Ephemeral workloads require always-on telemetry, not point-in-time audits. Zero Trust assumes compromise and validates every request, action, and data flow in real time.
How it’s done:
- Runtime Monitoring: Datadog Serverless Monitoring, Wiz, Palo Alto Prisma Cloud
- Behavioral Analytics: Detects anomalies (e.g., a Lambda suddenly calling unknown domains)
- Automated Threat Response: Policy-driven controls that block or quarantine suspicious functions
Leadership takeaway: Creates a “living audit” that satisfies regulators (HIPAA, PCI DSS, GDPR) by showing controls are enforced continuously, not just at audit checkpoints.
Pillar 3: Secure Data and Workload Segmentation
What it means: Zero Trust isolates functions, data flows, and event triggers to prevent lateral movement. No function or event source is trusted by default.
How it’s done:
- Micro-Segmentation: Illumio, Calico, service meshes like Istio or Linkerd
- Secured Event Triggers: Cloudflare API Shield, AWS KMS-encrypted buckets, OAuth2 for APIs
- Data Encryption Everywhere: In transit and at rest, with KMS or HSM-backed keys
Leadership takeaway: Even if an attacker compromises one serverless function, segmentation ensures the blast radius is contained, preserving resilience across multi-cloud environments.
Compliance Considerations for Regulated Industries
For organizations in regulated sectors, such as finance, healthcare, government, and critical infrastructure, cloud adoption is not just a technology shift; it’s a compliance challenge. Frameworks such as GDPR, HIPAA, PCI DSS, SOX, FedRAMP, and the EU’s NIS2 directive demand strict controls over data privacy, access, and auditability. At the same time, regulators are responding to cloud sprawl, insider threats, and cross-border data flows. Traditional perimeter defenses, such as firewalls and VPNs, cannot deliver the continuous assurance these laws require.
Compliance Challenges in the Cloud
- Data Sovereignty: Data replication across regions may breach GDPR and residency laws.
- Shared Responsibility: Cloud providers secure infrastructure, but enterprises remain accountable for workloads.
- Dynamic Environments: Containers and functions scale too fast for static audits.
- Third-Party Risks: SaaS, APIs, and vendors extend compliance far beyond direct control.
Why Compliance Demands Zero Trust
According to the 2025 State of Cloud Security Report (ETCISO.in), 61% of organizations struggle with security and compliance in hybrid and multi-cloud setups. Similarly, a Tailscale survey found 83% of IT and engineering teams bypass security controls to get work done, and 68% retained access after leaving an employer. This highlights the risks associated with weak identity and access management practices. Regulations such as HIPAA, PCI DSS, and GDPR demand encryption, least privilege, and clear audit trails. Zero Trust principles, identity verification, microsegmentation, continuous monitoring, and least-privilege enforcement align directly with these obligations.
How Zero Trust Makes Compliance Smarter
- Least Privilege: Access only to what’s needed, aligning with HIPAA and PCI DSS.
- Continuous Validation: Compliance as a state, not a quarterly event.
- Automation: Codified policies and audit-ready logs reduce human error.
- Safe Data Movement: Context-aware rules ensure compliance with GDPR and residency laws.
- Insider Risk Mitigation: MFA, just-in-time access, and analytics curb misuse.
Strategic Benefits
- Audit Readiness: Automated audit trails simplify regulator reviews.
- Regulator Confidence: Signals proactive, best-in-class security.
- Operational Efficiency: Automation reduces compliance overhead.
- Future-Proofing: Flexible enough to absorb NIS2, AI, and emerging privacy laws.
From Weakest Link to Managed Risk: Human Factors in Cloud Security
In 2019, a former AWS employee exploited stolen credentials to breach Capital One’s cloud environment, exposing sensitive data from over 100 million customers. The incident wasn’t caused by weak technology but was enabled by mismanaged access and insider knowledge. Cases like this highlight a hard truth: people remain the most unpredictable variable in cybersecurity.
Studies show that over 80% of breaches involve human error or misuse, from phishing and credential theft to insider abuse. In a cloud-first, distributed workforce model, human factors now play a decisive role in resilience. To address this, Zero Trust provides a structured framework for reducing people-driven risks.
Here are the seven pillars of human-centric Zero Trust that every leader should understand:
Why Humans Are the Weakest Link
Attackers don’t need to break systems when they can trick users. A single phishing email can hand over valid credentials, bypassing traditional defenses. Insider misuse is equally damaging, like a healthcare worker snooping on patient records, or an engineer downloading sensitive IP before resigning. Once inside, traditional perimeter defenses rarely stop lateral movement.
Identity as the New Perimeter
Zero Trust shifts defenses from networks to people. In this model, every user and device must prove identity and compliance every time.
Key elements:
- Multi-Factor Authentication (MFA): Passwords + tokens + biometrics = reduced reliance on static credentials.
- Adaptive Authentication: Context (location, device, time) dictates extra checks.
- Federated Identity: Unified authentication across AWS, Azure, Google Cloud, and SaaS reduces policy gaps.
Enforcing Least Privilege
Zero Trust enforces “just enough, just in time” access. By aligning permissions with roles, attributes, and temporary time windows, organizations minimize damage from stolen credentials or privilege creep.
Insider Threats in the Cloud Era
Insiders generally fall into three categories:
- Malicious: Employees or contractors intentionally stealing or sabotaging.
- Negligent: Well-meaning users mishandling data.
- Compromised: Accounts hijacked by phishing, malware, or credential stuffing.
Zero Trust addresses all three by treating trust as dynamic and fluid. Even after login, behavior is continuously monitored. Suspicious actions, such as mass downloads, unusual access times, or attempts that deviate from role norms, trigger alerts or automated responses.
Continuous Monitoring and Behavioral Intelligence
Modern Zero Trust integrates User and Entity Behavior Analytics (UEBA):
- A developer accessing code at 3 p.m. is normal; downloading gigabytes at 2 a.m. is not.
- A nurse reviewing 10 patient files per shift is expected; accessing 500 is a violation.
These insights, combined with automation, prevent insider risks from escalating.
Balancing Security and Productivity
Leadership must ensure controls don’t frustrate staff. Overly strict checks can cause “security fatigue.” The solution: risk-based policies that tighten only when anomalies arise, keeping everyday access seamless.
Strategic Payoff for Leadership
For CEOs and boards, Zero Trust delivers clear value:
- Reduced Credential Risk: MFA and adaptive authentication blunt phishing and credential stuffing.
- Containment of Insider Threats: Least privilege and monitoring limit damage.
- Regulatory Alignment: Directly supports HIPAA, PCI DSS, GDPR, and audit mandates.
- Agile Workforce: Enables secure, anywhere access without legacy VPNs.
Ultimately, Zero Trust transforms people from the weakest link into a managed risk. By making identity the cornerstone and embedding behavioral intelligence, organizations move from reactive breach response to proactive resilience, where trust is never assumed, only earned.
The Role of Automation and AI-Driven Threat Hunting in Enforcing Zero Trust
Zero Trust isn’t a static blueprint, but it’s a living framework that demands constant verification. In multi-cloud, hybrid, and serverless environments, billions of logs and signals are generated daily. Manual oversight cannot keep pace with this complexity. To make Zero Trust practical, automation and AI must be woven into enforcement.
.jpg)
Why Automation Matters
The principle of “never trust, always verify” requires continuous checks across users, devices, and workloads. At the scale of a Fortune 500 enterprise, this means billions of daily events. Automation ensures policies like least privilege and continuous authentication are enforced instantly and uniformly. Without it, gaps emerge that attackers exploit. For instance, in 2022, Uber’s breach was traced back to stolen credentials and delayed detection, a case where automated policy enforcement and anomaly alerts could have minimized damage.
AI-Driven Threat Hunting
Traditional security waits for alerts. Zero Trust flips this model: threats must be hunted proactively. AI enables this by:
- Correlating signals across cloud workloads, endpoints, and IAM logs to reveal coordinated attacks.
- Spotting anomalies such as unusual data transfers or lateral movement.
- Predicting risks using global threat intelligence.
Microsoft, for example, uses AI models across Azure to detect credential misuse within minutes, blocking billions of login attempts annually.
Strategic Benefits
- Speed: Automated responses reduce attacker dwell time from weeks to seconds.
- Consistency: Uniform enforcement across AWS, Azure, and GCP.
- Resilience: AI adapts to evolving attack tactics.
Human + Machine: The Balance
Automation and AI don’t replace people, they augment them. Machines handle scale and speed, while humans provide context, ethical oversight, and business alignment. The strongest Zero Trust programs operate as a partnership: AI enforces, humans interpret, and steer.
Zero Trust as the Blueprint for a Borderless Future
The old idea of a fixed network perimeter is gone. Workloads now run across AWS, Azure, GCP, and private data centers. Employees log in from airports, coffee shops, and home offices. Serverless apps scale up and down in seconds. In this reality, security can’t rely on walls and gates; it has to move with the business.
That’s where Zero Trust comes in. It’s not another tool you bolt on. It’s a way of thinking about security, a framework that constantly asks, “Can I trust this user, this device, this workload right now?” Access is granted based on identity, context, and posture, and not just whether someone is “inside the network.” This keeps policies consistent, no matter where workloads or users go.
For regulated industries, Zero Trust also makes compliance easier. Encryption is built in, audit trails are automatic, and least privilege is the default. People are still the primary source of most breaches, and implementing additional layers of protection, such as adaptive access controls, continuous verification, and behavior monitoring, can help mitigate this risk. When combined with automation and AI, Zero Trust becomes proactive, detecting anomalies and stopping attacks before they can spread.
The payoff goes beyond security. CIOs, CTOs, and CISOs get stronger protection and more freedom to innovate. Compliance costs decrease, operational risk diminishes, and new cloud strategies can be implemented with confidence.
In short, Zero Trust is no longer a nice-to-have. In a borderless world where agility is essential and threats are constant, it’s the operating model that defines resilience. Zero Trust isn’t just a security framework; it’s how enterprises stay resilient in a world without borders.
Ready to make Zero Trust more than a buzzword?
At Cogent Infotech, we help enterprises move beyond legacy defenses and build resilient, future-ready security frameworks. Whether it’s multi-cloud, hybrid, or regulated environments, our experts design, implement, and manage Zero Trust strategies that protect your business without slowing innovation.
Connect with us today to explore how we can help your organization accelerate its Zero Trust journey.







%402x.svg)


