What Is an Insider Threat? Breaking Down the Risk from Within



These days, insider threats constitute a growing business concern rather than merely an IT issue. In the last year, an astounding 83% of organizations reported at least one insider-related security breach, and over half reported an increase in frequency. The kicker? The average yearly cost to firms of mitigating these dangers has increased by 40% since 2019 to $16.2 million. Cloud-based operations, remote labor, and changing cyber threats provide additional obstacles to internalizing sensitive data security in 2025.
An insider threat, according to the Cybersecurity and Infrastructure Security Agency (CSA), is the potential for an insider to use their authorized access to compromise the department's mission, resources, personnel, facilities, information, equipment, networks, or systems, whether intentionally or unintentionally. Insider threats might manifest as violence, espionage, hacking, theft, or sabotage. Ex-employees and contractors of an organization may engage in actions that jeopardize the organization's interests for various reasons. Negligence, avarice, malevolent purpose, revenge, or profit-making are all possible motivations. An organization's reputation and revenue are significantly harmed, regardless of the reason. The U.S. State of Cybercrime Report states that 50% of data breaches and information leaks occur accidentally due to staff members' carelessness. Employee records are stolen and compromised for additional attacks in 40% of cases.
What Is an Insider Threat?
The potential for an insider to cause harm to an organization by exploiting their authorized access or knowledge of it is termed an insider threat. This damage might come from deliberate, inadvertent, or careless actions that compromise the availability, confidentiality, and integrity of the organization, its data, employees, or facilities. This general definition might be more appropriate and flexible for usage by the Cybersecurity and Infrastructure Security Agency's (CISA) clients and external stakeholders.
Insider threats are defined by CISA as the possibility that an insider will, knowingly or unknowingly, use their authorized access to compromise the department's mission, resources, staff, facilities, information, equipment, networks, or systems. The following insider behaviors could result in harm to the department as a result of this threat:
- Intelligence terrorism
- Unauthorised information leaking
- Corrupt practices, such as involvement in international organized crime
- Violence at work
- Deterioration or loss of departmental resources or competencies, whether deliberate or not
Insider Threat Impact on Sensitive Data

An organization's sensitive data may be seriously impacted by insider threats, which frequently have disastrous results. They could consist of:
- Monetary Loss: Insider threat-driven data breaches can lead to substantial monetary losses, including the loss of consumer information, private data, and intellectual property. Compared to an external attack, the cost of recovering from an insider threat-related incident is frequently significantly higher.
- Reputation Damage: Insider threats have the power to severely impact a company's standing, which can result in a decline in client confidence and lost business prospects. Companies sometimes can't recover from the consequences of a well-publicized insider data leak.
- Legal & Regulatory Penalties: If an organization is discovered to violate data security and data compliance rules, it may be subject to legal consequences as well as regulatory penalties for failing to protect sensitive data. Sanctions, fines, and even the revocation of operating permits are examples of this.
Why is Access Control Important For Insider Threat Programs?
Access control, or sets of guidelines that determine who has access to permissions are determined by their department and job duties.
According to the network security principle of least-privilege access, employees and other insiders should only be granted access to the information necessary for them to do their duties. For instance, a developer may need to modify the codebase, and a human resources specialist may need to view employee compensation data, but neither requires access to the other's files.
This contributes to the effectiveness of zero trust security as an IT security model. It entails rigorous identity verification for all individuals and devices attempting to access a company resource, even if they are already connected to the network. The potential consequences of all kinds of insider threats are reduced by restricting user and device access, much as the damage caused by losing a single credit card versus losing a wallet varies significantly.
What is Data Leakage?
The term "data leakage" describes the unapproved disclosure or transfer of private data from an organization to unprotected areas or outside groups. Numerous methods, including email, cloud storage, removable media devices, and even the physical theft of devices holding private information, can result in data leaks.
Employee carelessness, incorrect setups, and insufficient security measures are frequently the causes of data leaks. Sensitive information might, for instance, be unintentionally uploaded to an unprotected cloud storage service or accidentally emailed to the incorrect email address.
Strict data classification guidelines, encryption for data in transit and at rest, and access controls should all be put in place by organizations to stop data leaks. Finding and fixing any possible weaknesses in the company's data security procedures also requires regular security audits and employee training.
What Are the Characteristics of an Insider Threat?
External threats usually have financial incentives to steal information, demand ransom, and possibly resell that information on darknet marketplaces. An insider is more likely to inadvertently fall for a skilled phishing or social engineering attack, even if insider threats may have the same motivation. One common objective of a malevolent threat actor is to gain data to cause harm to the organization.
Because insider threats can take many different forms, it can be challenging to recognize the warning indications. The following are the most prevalent underlying traits of contemporary insider threats:
- Authorized Access: A person who has authorized access to an organization's premises, data, or systems, such as a partner, vendor, employee, or contractor is considered an insider threat.
- Difficult to Identify: Since the insider already has authorized access, it is difficult for security systems to discern between benign and malicious behavior, making insider threats difficult to detect.
- Diverse Strategies: Insider threats can use a variety of strategies to accomplish their objectives, ranging from credential theft and privilege escalation to data exfiltration and sabotage.
What Kinds of Insider Threats Should You Be Aware of?
Three groups can be distinguished: malicious insider, negligence, and compromised insider.

Malicious Insiders
These are people or organizations that have been permitted to access company data, but they utilize it dishonestly or destructively for financial benefit or out of resentment towards the company. Imagine frustrated employees or previous employees collaborating with other businesses or cybercriminals to disrupt company operations.
An example would be a former Yahoo employee who held a senior position and was accused of stealing important intellectual property from the firm just 11 days before he resigned, 45 minutes after accepting a job offer from a direct competitor. More than 570,000 pages of code, algorithms, and important company data are allegedly downloaded by the former employee, endangering some aspects of Yahoo's operations.
Tips for avoiding it:
- Create a well-defined access control policy: Make sure that the organization has a clear access control policy. Put in place explicit procedures to deny former workers access, prohibiting them from keeping track of outdated data or private information.
- Keep an eye out for odd activity: Keep track of odd activity times, including entering the building at odd hours or logging into the network. In order to quickly identify and resolve any issues, you should also monitor the transfer of massive amounts of data in sets.
Negligence
This kind of insider creates a risk to an organization by being negligent. In general, careless insiders are aware of security and/or IT policies, but they decide to disregard them, putting the company in danger. Misplacing or losing a portable storage device that contains sensitive data, letting someone "piggyback" through a secure entry point, and disregarding notifications to install security patches and new updates are a few examples.
Compromised Insiders
These risks are caused by credential theft, which is when someone poses as an employee of an organization. Social engineering or physical theft of an access card are two examples of how this might happen. The average cost to address these hazards is $804k per event, making them the most expensive.
Example: 133 user accounts were made accessible to attackers when a Mailchimp employee fell victim to a social engineering scam. Due to the fact that it was the third attack in less than a year, Mailchimp suffered greatly.
Tips to avoid it:
- Increase the security of your access by using password managers, two-factor authentication, and stringent access limitations. Increasing the strength of these elements improves defense against illegal access.
- Get regular training to protect yourself from social engineering and other dangers. Regular penetration testing will help you assess your security and improve resilience. These efforts support the development of a security-conscious culture in your company.
- Third-party and collusive threats, in which one or more insiders band together with an external threat actor to compromise an organization, are a subset of malicious insider threats. These events usually include hackers hiring one or more insiders to facilitate espionage, fraud, intellectual property theft, or all three. Third-party risks are often contractors or suppliers who are not formal members of an organization but have been given some level of access to buildings, systems, networks, or people to fulfill their tasks. Threats can be both direct and indirect.
Key Examples of Insider Threats
Yahoo
Yahoo was the target of an insider threat assault in May 2022. The organization's research scientist, Qian Sang, was offered a position by The Trade Desk, a competitor company. Sang copied over 570,000 pages of Yahoo's intellectual property, including details about Yahoo's AdLearn product, to his devices a few minutes later.
Yahoo didn't discover that Sang had stolen business information, including a competitive analysis of The Trade Desk, for several weeks. Yahoo said that Sang's activities stripped Yahoo of exclusive control over its trade secrets, and it sent him a cease-and-desist letter and filed three charges against him, including intellectual property data theft.
Microsoft
A data leak at Microsoft occurred in 2022 as a result of staff carelessness. Several Microsoft workers gave their login credentials to the organization's GitHub infrastructure, which was found by cyber security firm SpiderSilk. Access to Azure servers and perhaps other internal Microsoft systems may be made possible by this information.
Microsoft would not say whose systems were protected by these credentials. No one tried to access the sensitive data, according to an internal inquiry, and the business took steps to make sure this doesn't happen again. However, Microsoft might have been hit with €20 million in GDPR penalties if this error had revealed EU customer information.
Coca-Cola
An investigator discovered that an employee of Coca-Cola had transferred around 8,000 employees' data on a personal external hard drive. Coca-Cola informed staff members and provided free credit monitoring for a year after learning about the data compromise.
Benefits of Insider Threat Mitigation
Proactively responding to insider threats protects organizations from security concerns, financial losses, and compliance issues. Here are some of the main benefits of a strong mitigation program.
- Prevents Costly Data Breach - Eliminates unauthorized access controls and data loss protection solutions, lowering financial and reputational risk.
- Ensures Regulatory Compliance - Assists in meeting GDPR, HIPAA, and other security rules, hence avoiding legal penalties.
- Maintains Smooth Business Operations - Keeps security issues from affecting processes and productivity.
- Promotes a Security - Security-first culture by encouraging employee education, awareness, and proactive threat detection.
Five Common Indicators of Insider Threat Activity
When an insider attacks, they may need to compromise security mechanisms or put up hardware or software infrastructure to facilitate their or others' access to your system. Knowing how to recognize the techniques and tools they use allows you to detect the assault and take steps to mitigate it.
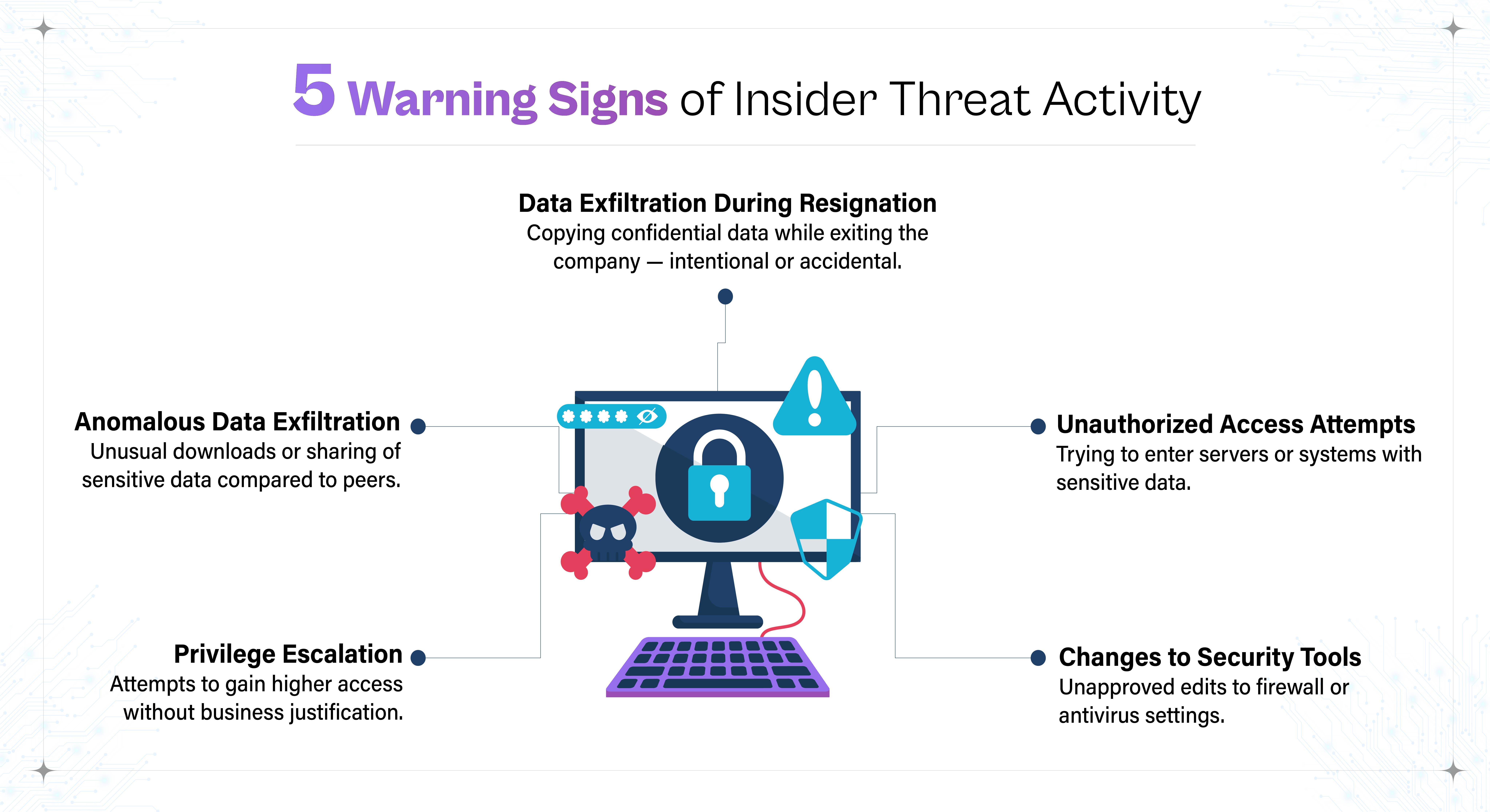
Here are some telltale symptoms.
- Privileges Escalation
Organizations typically preserve and regulate significant resources by delegating privileged access and functions to a small number of employees. If an employee attempts to escalate their rights without a clear business purpose, it may indicate a possible insider threat.
- Anomalous Data Exfiltration
Employees frequently access and exchange confidential data at work. However, if a user shares or downloads an extraordinary amount of sensitive material in comparison to their previous activity or peers in a comparable function, it may signify a data security crisis.
- Data Exfiltration
Data exfiltration frequently occurs in conjunction with resignations and can be either purposeful or unintentional. An unintended incident can be a departing employee inadvertently copying confidential data to keep track of their achievements in their career, but a malevolent incident might be knowingly downloading sensitive data for personal gain or to help them in their next employment. When resignations occur in conjunction with other unexpected activity, it may indicate a data security breach.
- Access Attempts to Servers or Devices With Sensitive Data
Anytime someone attempts to gain access to a sensitive region of your network, this could be considered an insider threat, especially since credentials supplied by the organization are frequently required.
- Unauthorized Changes to Firewalls & Antivirus Tools
Any change in the settings of a firewall or antivirus could be the result of an inside attacker attempting to get access to your machine.
Best Practices to Protect Against an Insider Attack
Protect Critical Assets
These might be physical or logical and include systems, technology, facilities, and individuals. Intellectual property, such as customer data for suppliers, proprietary software, drawings, and internal production methods, are also valuable assets. Develop a detailed grasp of your important assets. Ask questions like,
- What critical assets do we have?
- Can we prioritize our assets?
- What do we know about the current state of each asset?
Enforce Policies
Organizational policies should be documented so that they can be followed and misconceptions avoided. To avoid disclosing privileged content, everyone in the organization should be familiar with security procedures and understand their intellectual property rights.
Gain Visibility of All Your Data & Its Movement
You may have heard of preserving your most valuable assets, but it is simpler and more economical to regard all data as critical and monitor its movement accordingly. Every day, up to 34 users experience inadvertent data exposure, therefore securing all data as if it were vital helps reduce the chance of mistakenly moving sensitive information and creating a condition for IP theft. Ensure that staff understand that monitoring data transfer to untrusted locations is not the same as surveillance. Instead of tracking keystrokes, photographing screens, monitoring performance, or engaging in other invasive activities, a corporation monitoring its data benefits both people and the company by protecting innovation and competitive advantage.
Prevent An Insider Threat With Mimecast
Mimecast offers cloud-based services for email security, continuity, and archiving that are administered from a single pane of glass, lowering the cost and complexity of advanced threat prevention. Mimecast Internal Email Protect, a security monitoring and remediation service for internally generated email, can help detect and prevent insider threats. As part of Mimecast's email security service, this insider threat program allows you to monitor, detect, and mitigate email-borne security threats that originate within your organization. Internal Email Protect checks all emails, as well as attachments and URLs, for malware and harmful links. Mimecast can also use content filtering to detect insider threats and implement data leakage prevention services.
Manage Access to Limit User Privileges
Insider threats use authorized access to steal data or disrupt networks. Companies must limit authorized access to persons for genuine business purposes. When employees leave, systems should withdraw their privileges and de-escalate any temporary administrative privileges. NordLayer can help you improve network access control. Cloud Firewalls and Device Posture Security are tools that let you implement Access Control Lists (ACLs). These tools enable security teams to segregate network access permissions and reduce exposure. Users have access to critical resources while remaining restricted from other sensitive assets. This lowers the likelihood of malicious insiders causing damage.
Ensure Strong Authentication & Access Management
Ensuring and implementing MFA and strong passwords as part of the password policy can help secure access to systems and information. MFA dramatically lowers the attacker's ability to access sensitive information, even if they have the necessary credentials. They should also be examined regularly and altered whenever a person in charge of a given security level changes positions or is terminated.
Use Data Loss Prevention Technologies
DLP systems enable organizations to monitor and prevent the incorrect sharing of various types of data. DLP stops insiders from sharing or stealing information by filtering high-risk data flows or limiting data and file transfers outside of the network.
Multi-Factor Authentication
Multi-factor authentication is a widely recognized best practice for safeguarding important assets and effectively managing access to them. Another alternative is to employ a zero-trust security architecture when access to a crucial asset is always limited and requires further approval or user identification verification.
The Role of Technology In Insider Threat Prevention
- User & Entity Behaviour Analytics: In the digital age, technology is crucial for identifying insider threats. User and entity behaviour analytics uses machine learning and advanced analytics to investigate user and entity behaviors. UEBA provides insights into spotting anomalies, allowing you to quickly detect and respond to potential attacks.
- Solutions for Data Loss Prevention: Insider attacks commonly target data, which highlights the importance of data loss prevention solutions. DLP technology enables you to monitor and secure sensitive data by preventing unauthorized access, sharing, or exfiltration. DLP methods can significantly increase data security.
- Endpoint Detection & Response: Insiders regularly use endpoints, such as laptops and mobile devices. Endpoint detection and response systems enable real-time monitoring and rapid reaction. It helps you identify and neutralize threats at their source, thereby reducing potential damage. Tools for identifying insider threats: There are numerous specialized solutions available in the cybersecurity field for detecting insider threats. It offers a variety of insider threat detection approaches that may help you improve your security posture. These solutions, ranging from network traffic analysis to privileged user monitoring, provide targeted defenses against both malicious and non-malicious insider attacks.
Conclusion
The struggle against insider dangers cannot be won decisively. Instead, it is an ongoing process that requires knowledge, flexibility, and a commitment to security. Insider threats can come from both malicious intent and unintentional activity, thus it is vital to constantly strengthen your defenses. It is time to improve your organization's insider threat defenses. To increase your cybersecurity posture, implement the appropriate techniques, technology, and best practices. Create an awareness, trust, and accountability culture in your organization.
Thus, by taking a proactive approach to insider threats, you protect your organization and demonstrate your commitment to safeguarding your data, reputation, and the trust of your customers and partners. Your focus on insider threat avoidance indicates your resilience and dedication to a secure future in an ever-changing digital landscape.
Contact Cogent Infotech today if you need cybersecurity services.







%402x.svg)






