Compliance Isn’t Optional: Preparing for a Seamless IT Audit in 2025



In today’s digital world, an IT audit checklist isn’t a box to tick. It’s a real test of how securely and responsibly a business operates. Cloud-native environments, AI-driven systems, and cyber threats are reshaping IT to continuous, high-stakes evaluations that impact compliance, resilience, and trust. Regulators now expect enterprises to prove compliance at any moment.
Failing an audit results in multimillion-dollar penalties, operational disruption, and reputational damage. To avoid gaps, enterprises are moving from reactive fixes to proactive compliance strategies. That means embedding automated compliance monitoring into daily workflows, aligning with DevOps and SecOps, and applying Zero Trust governance. They create a system that is audit-ready. This shift transforms audits from stressful, last-minute firefights into seamless processes.
Frameworks such as SOC 2 compliance cloud and HIPAA cloud security have become non-negotiable. Audit readiness in 2025 is no longer optional. It’s a benchmark of business maturity that builds lasting trust with customers, partners, and regulators. Let’s explore these frameworks in detail.
The Compliance Landscape: Frameworks That Matter in 2025
Navigating IT compliance is more than a regulatory requirement. It’s a foundation that defines security, privacy, and risk management. In a cloud-native and AI-driven environment, businesses must understand not only what frameworks exist but why they matter for operational resilience and audit readiness. To meet these challenges, compliance frameworks provide structured guidance.
The five major frameworks are:
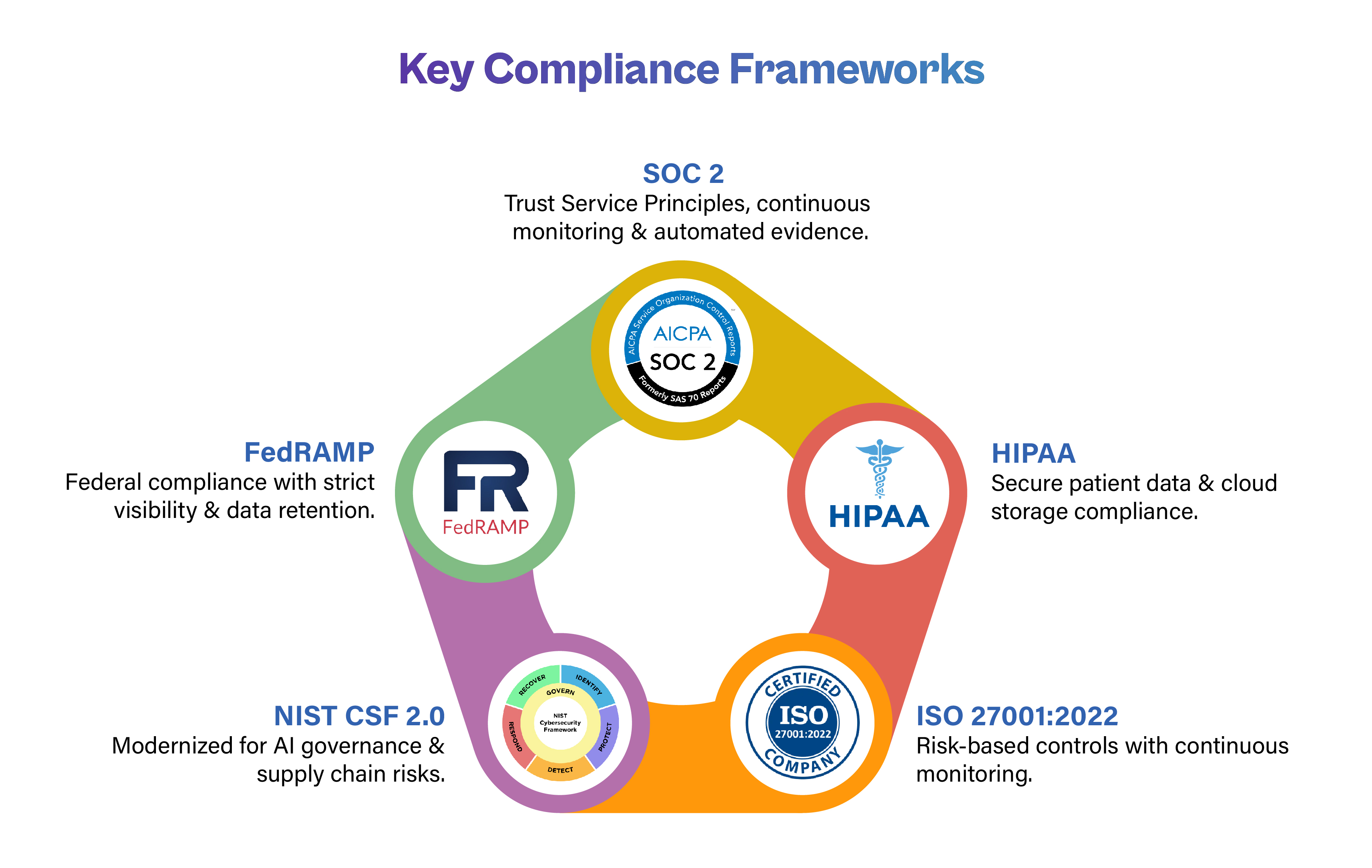
SOC 2: Trust Service Principles in a Cloud-Native World
SOC 2 compliance cloud remains the basis for cloud service providers and SaaS platforms. Built around the Trust Services Criteria: security, availability, processing integrity, confidentiality, and privacy. For most enterprises, SOC 2 is a trust signal that strengthens customer relationships.
Annual, point-in-time audits are no longer enough. Customers and regulators expect near real-time assurance that security controls are working continuously. This shift has made continuous monitoring, automated evidence collection, and integration with platforms like Drata or Vanta essential to staying "always audit-ready”.
Audit Insight: Preventing configuration drift in dynamic, multi-tenant environments.
HIPAA: Safeguarding Healthcare in the Cloud
HIPAA remains the cornerstone of healthcare compliance. It governs how Protected Health Information (PHI) is managed and secured. As healthcare delivery extends into telehealth platforms and SaaS ecosystems, PHI flows across hybrid and multi-cloud environments, raising the complexity of compliance. the need for automated compliance monitoring.
In 2025, regulators are cracking down on insecure APIs, weak access controls, and misconfigured cloud storage. Meeting HIPAA standards now requires encryption at rest and in transit, and automated audit logs. Along with automated monitoring, airtight access governance across distributed systems.
Audit Insight: Demonstrating airtight protection across distributed systems without interrupting clinical workflows.
ISO 27001:2022 : Updated Controls & Risk-Based Approach
ISO 27001 remains the global benchmark for Information Security Management Systems (ISMS). It’s the language of credibility and market access. The 2022 update sharpened its focus on risk-based controls, cloud services, and supply chain threats.
ISO certification signals credibility, regulatory alignment, and resilience in cross-border operations. The standard’s risk-based approach demands security integration across DevOps pipelines, change management processes, and day-to-day business operations.
Audit Insight: Maintaining a living inventory of risks, policies, and governance evidence along with technical controls.
NIST CSF 2.0: Modernized for Evolving Threats
The NIST Cybersecurity Framework (CSF) is a widely adopted model for resilience. The 2.0 update, released in 2024, strengthens focus on supply chain security, governance, AI risks, and continuous monitoring. For auditors, NIST CSF 2.0 maps resilience across Identify, Protect, Detect, Respond, and Recover functions.
NIST CSF 2.0 has become a cornerstone for both public and private sectors, often required for federal contracts. Enterprises also adopt it as a maturity benchmark and governance model, linking cybersecurity controls to business outcomes.
Audit Insight: Mapping NIST CSF controls to other frameworks (SOC 2, ISO, HIPAA) without duplicating effort.
FedRAMP – Federal Cloud Compliance for Vendors
For cloud service providers working with U.S. federal agencies, FedRAMP certification is mandatory. It enforces rigorous security controls based on NIST standards and requires monthly reporting, continuous monitoring, and coordination with sponsoring agencies.
Beyond federal contracts, FedRAMP is shaping expectations in the private sector. Large enterprises need FedRAMP-aligned controls from vendors to ensure secure cloud adoption.
Audit Insight: FedRAMP’s demands go beyond checklists. It requires disciplined execution.
While frameworks outline what’s required, the key is embedding compliance into daily operations. Consistent application of controls keeps your enterprise prepared for audit-ready year-round.
Building Always-Audit-Ready Environments
Today, compliance can’t be a once-a-year fire drill. The era of scrambling for logs, screenshots, and scattered evidence at the last minute is over. Customers, regulators, and auditors now expect continuous assurance. Enterprises that can’t deliver risks face regulatory fines, damaged trust, and lost opportunities.
Why “Last-Minute Compliance” Fails
Reactive compliance creates unnecessary risk and chaos. Common pitfalls include:
- Incomplete evidence – Missing keylogs, access records, or policies often surface under audit pressure.
- Manual, error-prone processes – Spreadsheets, email chains, and ad hoc reporting make mistakes inevitable.
- Delayed reporting – Late evidence pulls lead to inconsistencies, findings, and higher audit costs.
The outcome is predictable: higher audit costs, prolonged timelines, and credibility loss with both regulators and customers. Auditors demand real-time visibility, not after-the-fact documentation. Without proactive readiness, efficiency drops and credibility erodes.
Mapping Controls to Business Processes and Systems
True audit readiness starts with making compliance part of the way the business runs:
- Identify critical processes and data flows – Understand where sensitive data lives, how it moves, and who has access.
- Map frameworks to workflows – Align SOC 2 compliance cloud, HIPAA cloud security, ISO 27001, NIST CSF, or FedRAMP requirements with daily operations.
- Automate evidence collection – Replace screenshots and spreadsheets with dashboards that continuously capture logs, configurations, and access records.
This approach reduces audit friction. By ensuring automated compliance monitoring, and turns evidence into a living system that’s always up to date.
Integrating Compliance into DevOps & SecOps Workflows
Modern IT environments move at cloud speed, and compliance must keep up. By embedding compliance into DevOps and SecOps workflows, enterprises shift from point-in-time checks to continuous enforcement:
- CI/CD pipelines automatically capture deployment logs, security checks, and configuration changes as audit artifacts.
- Automation platforms like Drata, Vanta, and Wiz provide real-time monitoring, flagging drift or violations before they become audit issues.
- Shift-left security ensures compliance and security checks happen early in development, long before production.
The results are faster audits, fewer gaps, and real-time proof of security posture.
Audit Documentation in Cloud-Native Environments
Modern IT environments have redefined how audits must be approached. In these environments, audit evidence is no longer static. It is fluid, distributed, and changing, making it harder to collect, retain, and present in a defensible way. Without disciplined processes, enterprises risk running into delays, gaps, and compliance setbacks.
The solution: treat audit documentation as a live, evolving asset, not a static folder. With the right tools and processes, cloud-native environments can make audits faster, stronger, and more reliable.
Storing, Versioning, and Retrieving Evidence
Audit readiness starts with organization and traceability. Best practices include:
- Centralized storage – Keep logs, policies, and configurations in a single, auditable repository.
- Versioning & time-stamps – Every change in systems or policies must be recorded, enabling auditors to trace earlier states.
- Searchable records – Evidence must be retrievable to respond to auditor inquiries, reducing delays and friction.
This structure ensures traceability, accelerates responses, and strengthens defensibility in front of auditors.
Automation in Evidence Gathering
Manual evidence collection is too slow and error-prone for cloud-native environments. Automation reduces errors and ensures audit-ready data.
- API-driven data feeds – automatic logs collect system, access events, and configuration changes.
- Real-time alerts – Identify compliance drift before it becomes an audit issue.
- Audit-ready reporting – Generate evidence on demand without last-minute scrambling
Platforms like Drata, Vanta, and Wiz (2025) provide automated compliance monitoring pipelines that gather and validate evidence year-round, reducing human error and proactive alerts before an issue escalates.
Secure Storage & Role-Based Access
Audit documentation is more than accessibility, it’s also about protection. Sensitive evidence (access logs, security configs, customer data flows) must be safeguarded with Zero Trust governance principles.
- Role-based access control (RBAC) – Ensure only authorized users can access or modify evidence.
- Encryption at rest and in transit – Protect logs and records from interception or tampering.
- Audit trails – Maintain a record of who accessed or modified records, supporting defensibility in front of auditors and regulators.
Zero Trust governance approach strikes a balance between security and accessibility.
Year-Round Compliance Monitoring Tools
In cloud-native environments, documentation alone isn’t enough to guarantee audit readiness. enterprises need tools that watch systems continuously and enforce controls automatically. This is where modern compliance monitoring tools come into play.

Platforms like Drata and Vanta handle SOC 2, ISO, and HIPAA monitoring, while Wiz keeps an eye on cloud security posture. When these platforms are integrated into DevOps, SecOps, and IT workflows sets the stage for always-audit-ready environments.
Automated Framework Monitoring (Drata, Vanta)
Solutions like Drata and Vanta automate compliance across SOC 2, ISO 27001, HIPAA, and other frameworks. They:
- Evidence collection: Collect and update evidence automatically across cloud services, SaaS apps, and identity systems.
- Alert teams: Send instant team alerts, flag policy violations, and control drift
- Maintain real-time dashboards: Provide dashboards for auditors, executives, and compliance teams, making reporting fast and transparent.
By embedding compliance into daily operations, these tools eliminate last-minute fire drills and replace them with continuous assurance.
Cloud Security Posture Management (Wiz)
Where Drata and Vanta track frameworks, Wiz strengthens security and compliance through cloud security posture management (CSPM). Its capabilities include:
- Continuous scanning of multi-cloud and hybrid environments for misconfigurations and vulnerabilities.
- Prioritizes risks to focus resources where they matter most.
- Aligns technical controls with regulatory frameworks, bridging the gap between cloud operations and audit requirements.
This ensures that cloud security and compliance are not siloed but managed as one integrated practice.
Strategic Tool Integration
Choosing the right tool is only half the equation, real value comes from seamless integration into workflows:
- DevOps and SecOps pipelines: Evidence and alerts flow directly into daily operations.
- Ownership-driven alerts: Notifications are tied to responsible teams for quick action.
- Cross-team visibility: Compliance, IT, and security teams operate from a shared source of truth.
The Strategic Edge
enterprises that adopt continuous compliance monitoring gain much more than audit readiness:
- Operational efficiency – Lower manual workload and reduced audit costs.
- Risk visibility – Early detection of gaps before auditors or regulators identify them.
- Business resilience – The Ability to demonstrate compliance and security posture at any moment builds trust with customers, partners, and regulators.
Instead of chasing audit deadlines, these enterprises operate in a living, auditable ecosystem that evolves in sync with technology and regulation.
Zero Trust as a Compliance Enabler
Audit readiness involves more than collecting evidence before an assessment. It requires a security model that supports compliance in daily workflow. Traditional security models that rely on a fixed perimeter don’t work in modern cloud-native environments, where risks evolve and regulators expect faster, cleaner answers.
This is where Zero Trust comes in. Built on identity-first access, continuous verification, and least-privilege enforcement. It strengthens security while embedding compliance into daily operations. Every login, every access request, and every permission is verified and recorded.
Rather than treating compliance as a burden, Zero Trust turns it into a byproduct of stronger security helping businesses stay protected while staying audit-ready.
Identity-First Security and Continuous Verification
Zero Trust assumes no implicit trust. Whether users are on-premises, remote, or operating in the cloud. Core principles include:
- Verify every request – All users, devices, and workloads are authenticated and authorized.
- Least-privilege access – Permissions are strictly limited to what’s necessary for each role.
- Continuous monitoring – Logs, system changes, and session activity are tracked in real time.
This approach produces complete, auditable logs of access events, directly supporting frameworks like SOC 2, HIPAA, ISO 27001, and FedRAMP.
Mapping Zero Trust to Compliance Requirements
One of the strongest advantages of Zero Trust is how naturally it aligns with compliance requirements. By mapping Zero Trust practices to regulatory controls, enterprises can eliminate evidence gaps and demonstrate proactive governance. Making compliance becomes an ongoing outcome of daily security operations. It follows
- Identity Verification – Every login is verified and logged, creating a clear record that proves only authorized users had access (meets SOC 2, HIPAA).
- Least Privilege – Users get only the access they need, reducing both security risk and audit exceptions (supports ISO 27001, NIST).
- Micro-Segmentation – Sensitive data and systems are isolated, making it easier to demonstrate compliance with strict access boundaries (aligns with HIPAA Security Rule).
- Continuous Monitoring – Compliance evidence is generated automatically and in real time, rather than waiting for audit snapshots (required by SOC 2, FedRAMP).
Case Example: Mayo Clinic: Zero Trust for Healthcare and Compliance
The Mayo Clinic, a global leader in healthcare, needed to protect millions of patient records and meet strict HIPAA requirements while expanding into telehealth. To strengthen security without disrupting care, it adopted a Zero Trust framework across its network.
Key Steps Taken:
- Enforced strong identity-centric authentication for staff and partners.
- Applied micro-segmentation to isolate sensitive systems like electronic health records (EHR).
- Enabled secure remote access for telehealth services.
- Introduced continuous risk scoring to adjust access dynamically.
Impact & Outcomes:
- Patient data safeguarded with reduced breach risks.
- Audit readiness improved through continuous logging and monitoring.
- Compliance posture strengthened without slowing clinical operations.
- Telehealth expanded securely, supporting innovation in care delivery.
Strategic Advantage
Zero Trust is more than a cybersecurity framework, it’s a compliance enabler. By embedding compliance into everyday access and verification processes, enterprises can:
- Reduce audit scope and effort with real-time, verifiable evidence.
- Strengthen security posture through consistent enforcement of controls.
- Enable operational agility by aligning security and compliance.
- Enhance governance when paired with automated monitoring tools like Drata, Vanta, or Wiz.
When combined with automated monitoring tools like Drata, Vanta, and Wiz, Zero Trust turns compliance into a continuous, business-aligned capability, making enterprises always audit-ready, resilient, and competitive.
IT Audit Readiness Checklist for 2025
Maintaining IT audit readiness requires a structured, actionable checklist. Leveraging automated compliance monitoring ensures accurate evidence collection, reduces errors, accelerates audit cycles, and guarantees compliance across SOC 2, HIPAA, ISO 27001, NIST CSF 2.0, and FedRAMP frameworks. This checklist consolidates key focus areas.
Must-Have Evidence Categories
To be audit-ready, enterprises should maintain evidence across these core categories:
- Access Controls: User roles, permissions, authentication methods, and audit logs
- Change Management: Documentation of system updates, patches, and configuration changes
- Data Protection & Privacy: Encryption standards, data retention policies, and GDPR/HIPAA compliance records
- Incident Response & Security Monitoring: Logs of incidents, mitigation steps, and post-mortem analyses
- Training & Awareness Records: Evidence that employees receive ongoing compliance and security training.
Integration with Tools & Automation
Modern IT audit readiness relies on automation and continuous monitoring:
- Automated SOC 2 / ISO / HIPAA Monitoring: Platforms like Drata and Vanta maintain evidence in real-time
- Cloud Security Posture Management: Tools like Wiz detect misconfigurations and risks continuously
- API-Based Evidence Collection: Reduces manual effort and ensures logs, reports, and metrics are consistently available
Running a Mock Audit
A proactive strategy includes simulated audits to identify gaps before external review. Steps include:
- Assign an internal or external team to act as auditors.
- Test retrieval of evidence for policies, logs, and configurations.
- Verify automated monitoring reports and dashboards are complete and accurate.
- Document gaps, assign owners, and remediate before the actual audit.
Common Pitfalls & How to Avoid Them
Even with a checklist, audits can fail if common pitfalls are overlooked:
- Incomplete Evidence Mapping: Use automated tools to ensure all systems and processes are covered.
- Lack of Vendor Verification: Maintain up-to-date third-party compliance reports and contracts.
- Over-Reliance on Manual Processes: Integrate automation into monitoring, evidence collection, and reporting.
- Disconnected Workflows: Align DevOps, SecOps, and ITSM workflows to ensure all compliance activities are traceable.
By following this checklist, enterprises move from reactive audits to structured, strategic readiness. Auditors gain clear visibility into controls and processes, reducing findings and audit duration. Teams also benefit from operational efficiencies, stronger security posture, and confidence in meeting emerging regulatory demands.
Conclusion: Turning Compliance into a Competitive Advantage
In 2025, compliance is no longer a checkbox, it’s a strategic differentiator. Companies that weave audit readiness into daily operations lower their risk, protect against cyber threats, and build stronger trust with customers, partners, and regulators.
Modern IT environments: cloud platforms, hybrid systems, and AI-powered workflows, require more than annual checklists. They demand continuous monitoring, automated evidence collection, and built-in security checks. With Zero Trust governance, every user, device, and system is verified in real time, creating instant audit trails. This transforms audits from stressful, last-minute scrambles into routine, predictable reviews.
The payoffs are clear: shorter audit cycles, fewer disruptions, stronger security, and greater confidence. In a fast-moving digital market where regulations are tightening, being audit-ready signals that an organization is reliable and resilient.
Looking ahead, automation and Zero Trust make it easier to adapt to new laws, evolving cyber risks, and future technologies. Compliance is no longer a defensive cost; it’s a proactive strategy that strengthens competitiveness. The path is clear: start automating monitoring, embed Zero Trust, and build a culture of year-round readiness.
Thus, compliance done right isn’t just about passing audits, it’s about proving resilience and earning trust.
Stay Audit-Ready with Cogent Infotech
In a world where compliance is a continuous journey, Cogent Infotech helps enterprises embed automation, align with leading frameworks, and build trust through resilient, audit-ready operations. Whether you’re navigating SOC 2, HIPAA, ISO 27001, NIST CSF 2.0, or FedRAMP, our experts ensure you’re prepared not just for the next audit, but for the future of digital compliance.
Partner with Cogent Infotech today and turn compliance into a competitive advantage.







%402x.svg)


