Zero Trust Metrics that Matter: How to Build a Scorecard for Security Maturity



Zero Trust has evolved from a cybersecurity philosophy into a practical, metrics-driven framework essential for securing today’s dynamic, cloud-native environments. To measure Zero Trust maturity effectively, organizations must implement trust scores, policy enforcement tracking, and real-time telemetry across users, devices, workloads, and networks. Using established models like NIST, CISA, and Forrester, alongside behavioral analytics and MITRE ATT&CK mapping, enables continuous validation and adaptive risk management. A well-structured Zero Trust scorecard transforms security operations, providing visibility, accountability, and alignment with business goals, while future-proofing your defense strategy in hybrid, multi-cloud, and remote-first infrastructures.
Zero Trust Metrics That Matter: How to Build a Scorecard for Security Maturity
The age of perimeter security is over. In a cloud, remote-enabled world, Trust isn't a static attribute. It's dynamic, contextual, and continuously validated. You've implemented Multi-Factor Authentication (MFA). Endpoint Detection and Response (EDR) is now operational. You've segmented your network and deployed policy-based access controls. Each of these steps enhances your security posture, but without a guiding framework, they function in silos.
Enter Zero Trust, the guiding principle for modern cybersecurity. It brings coherence, anchoring security in the principle of constant verification. Its core tenet is never trust, always verify. Zero Trust builds on existing security layers, shifting the focus from one-time checks to continuous validation.
However, while the philosophy is clear, its execution remains cloudy, especially regarding measurement. For security practitioners, the real challenge with Zero Trust is accountability. It isn't a single product, it's a dynamic, evolving framework. And like any strategic initiative, it needs a scorecard: a structured way to track progress across identity, device, workload, and network controls.
So, how do you quantify Trust? How do you validate that your Zero Trust strategy is working, evolving, and protecting the business?
To answer these questions, security leaders must move beyond ad hoc implementations and adopt a data-driven approach focused on trust scoring, maturity tracking, and outcome-based reporting.
In this article, we'll explore how to build a Zero Trust scorecard, leveraging maturity models, trust scores, and meaningful security KPIs to prove and improve your Zero Trust implementation. Because in the future of cybersecurity, the organizations that measure well will lead well.
Understanding Zero Trust
Zero Trust starts as a philosophy, "never trust, always verify." However, to be effective, it must evolve into an operational strategy. That means embedding Zero Trust principles into every layer of the security architecture: identity, devices, workloads, networks, and data.
Unlike traditional perimeter-based models, which assume internal traffic can be trusted. Zero Trust is a modern cybersecurity strategy rooted in the idea that nothing should be trusted by default, not users, devices, or workloads, even if they're inside the network. Every access request is treated as potentially hostile until explicitly verified.
This model relies on strict identity verification, least-privilege access, and continuous monitoring. Its goal is to ensure that only the right entities access the right resources at the right time and under the right conditions.
This approach is especially well-suited for today's hybrid environments, where users work from anywhere, on any device, often through complex cloud-based infrastructures. Importantly, Zero Trust isn't a single tool or platform, it's a mindset supported by technologies and practices designed to reduce risk and limit the damage of potential breaches.
Importantly, Zero Trust is not a binary goal but a maturity journey. Organizations adopt their principles at different speeds and depths across departments and systems. To ensure progress, they need a way to measure how well these principles are being operationalized, enter the Zero Trust scorecard.
Why the Importance of Measuring Zero Trust Maturity Matters
Zero Trust isn't implemented overnight. It evolves in stages and often unevenly across the organization. That's why measuring maturity is essential. Without measurement, it's impossible to benchmark progress, identify areas of weakness, or align with industry standards.
A Zero Trust maturity model helps organizations understand progress. It guides the shift from reactive or fragmented practices to fully integrated, automated strategies. It assesses readiness across key pillars like identity, devices, applications, and data and tracks how well policies are enforced and risks are mitigated.
Most importantly, maturity metrics translate technical progress into business value. They help justify investments and secure ongoing executive support.
The Challenge of Demonstrating Effectiveness
Proving the effectiveness of cybersecurity efforts is notoriously difficult. Traditional financial or sales KPIs (key performance indicators) measure clear outcomes. Security metrics, by contrast, often measure what didn't happen, the breach that was prevented, the attack that didn't succeed.
Zero Trust adds another layer of complexity. It's proactive by design, meant to reduce exposure and contain breaches before they escalate. But without clear metrics, it's difficult for security teams to demonstrate impact. Executives want to understand the return on investment. Compliance teams need evidence of progress. Operational teams require feedback to fine-tune performance.
That's where the Zero Trust scorecard proves its value. It turns a broad vision into a quantifiable, actionable strategy.
Defining Key Terms
Before building a scorecard, it's essential to clarify key terms central to Zero Trust:
Zero Trust Architecture (ZTA)
A conceptual framework that outlines the principles and components required for Zero Trust. It includes identity verification, least-privilege access, and continuous monitoring across all layers.
Trust Scores
Dynamic metrics that reflect how trustworthy a user, device, or workload is. These scores adjust based on behavior, compliance, and risk signals and inform real-time access decisions.
Telemetry
The real-time data collected from systems, networks, and endpoints. Telemetry feeds into trust scores and helps enforce adaptive security policies.
Policy Engine
The decision-making component that uses trust scores and contextual signals to determine whether to grant, deny, or elevate access.
These elements are foundational for building a metrics-driven Zero Trust program. They form the basis for what gets measured, how it's measured, and how those measurements influence real-time security decisions.
Who Benefits from Zero Trust Metrics and Why It Matters
Measuring Zero Trust maturity isn't just a best practice, it's a strategic necessity. A well-designed scorecard enables organizations to identify gaps, track improvements, and align cybersecurity goals with business objectives. It provides tangible evidence of risk reduction and return on investment.
Beyond internal use, a scorecard's value lies in its ability to speak to multiple audiences. For CISOs and security teams, it offers detailed insights into operational performance and policy enforcement. Executives and board members benefit from a high-level view of progress and risk posture, helping them make informed decisions about budgets and priorities. Meanwhile, compliance and audit functions rely on measurable indicators to verify that security controls meet regulatory requirements.
In short, measuring Zero Trust maturity ensures that organizations stay secure and prove how and why their security investments make a difference.
Security maturity isn't just a benchmark, it's a business imperative.
Zero Trust Maturity Models: Frameworks for Progress
Implementing Zero Trust is a long-term commitment, not a checkbox exercise. It demands a systematic transformation of how your organization approaches security, rooted in continuous validation, context-aware decision-making, and architectural evolution. Organizations need a structured way to assess their progress to ensure that this commitment leads to tangible, measurable improvement. That's where Zero Trust maturity models come in.
These frameworks provide a roadmap for evolving your security posture, from basic access controls to intelligent, automated threat detection and response. Understanding how these models work, and selecting the right one for your organization is key to building a scorecard that drives strategic outcomes.
Overview of Leading Models
Several influential organizations have developed maturity models to help define and guide Zero Trust implementation:
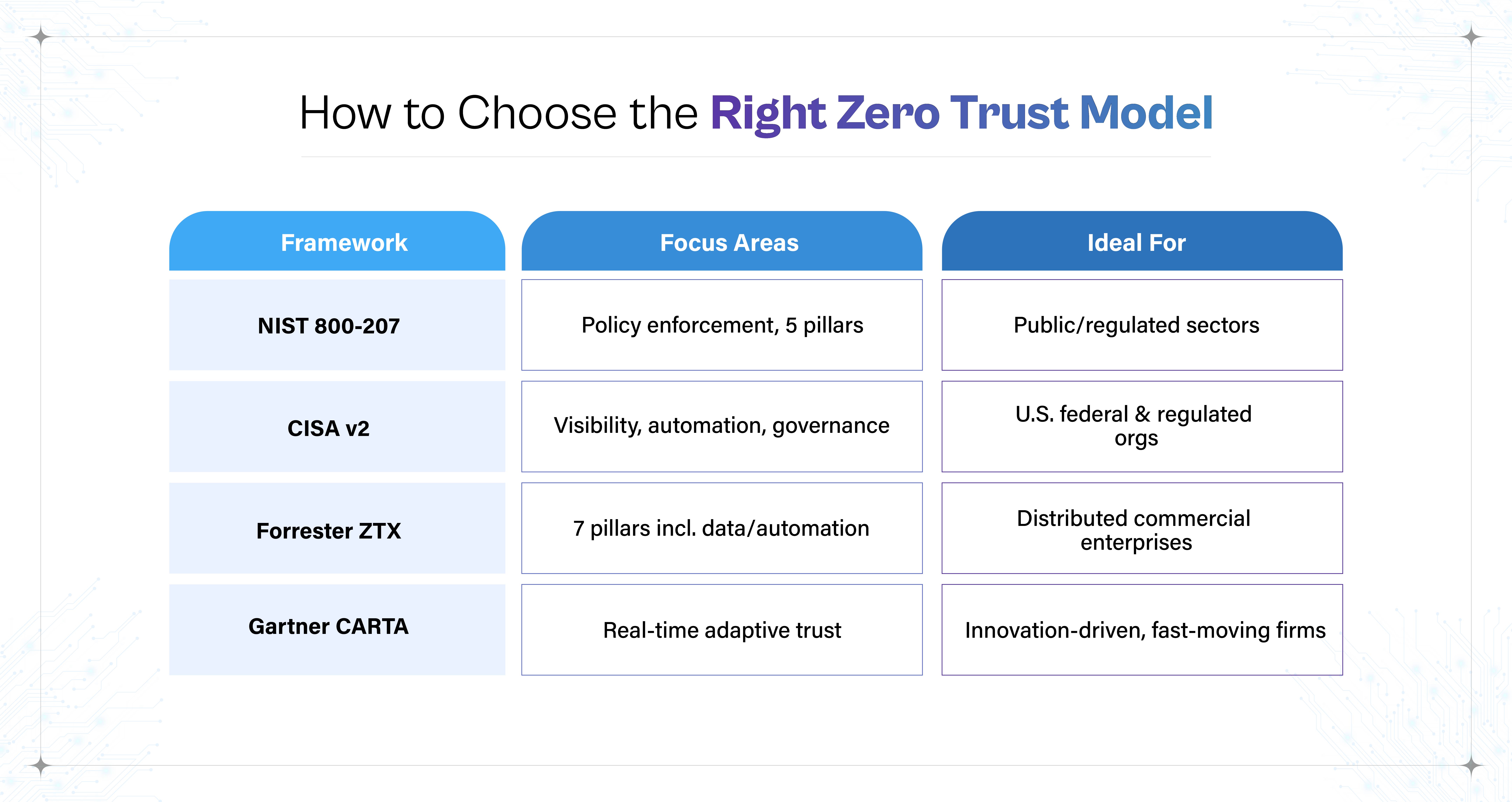
NIST SP 800-207 & SP 500-204 (Zero Trust Architecture & Maturity Model)
These models are adopted in both the public and private sectors. They emphasize continuous verification, dynamic policy enforcement, and integration across five pillars: Identity, Device, Network/Environment, Application Workload, and Data.
Each pillar can be evaluated across different maturity levels, from manual and siloed processes to integrated, automated controls. NIST's approach is robust because it focuses on policy enforcement points (PEP) and policy decision points (PDP) ensuring that trust decisions are made and enforced consistently.
CISA Zero Trust Maturity Model (v2)
Developed by the Cybersecurity and Infrastructure Security Agency, this model aligns with the U.S. federal zero-trust strategy. CISA evaluates progress using four maturity levels: Traditional, Initial, Advanced, and Optimal, across five security pillars. It also adds cross-cutting capabilities like visibility, automation, and governance, providing a clear trajectory toward Zero Trust goals.
Forrester ZTX Framework
Developed by John Kindervag (the originator of Zero Trust), focuses on commercial enterprises. This model organizes Zero Trust around seven pillars: data, people, devices, workloads, networks, automation, and visibility/analytics. It's beneficial for organizations with distributed environments and diverse access patterns.
Gartner's CARTA Model (Continuous Adaptive Risk and Trust Assessment)
Rather than a fixed maturity framework, CARTA emphasizes continuous assessment of Trust and risk. It focuses on adaptive security, AI-driven analytics, and behavior monitoring. It elevates automation, machine learning, and telemetry-based decisions as strategic priorities.
Each of these models brings a unique perspective. Together, they reinforce a shared message: Zero Trust is a journey, and maturity is the key to making that journey measurable and impactful.
The Zero Trust Journey: From Initial to Optimized
Most Zero Trust maturity models follow a staged approach, with organizations progressing through five defined phases as they implement more sophisticated controls:
- Initial: Security is reactive and siloed. Trust is implicit, and access controls are minimal or inconsistent.
- Developing: Some identity and access policies exist, but enforcement is not uniform. Visibility is limited.
- Defined: Policies and tools are standardized across the environment. Trust decisions are based on multiple signals.
- Managed: Security is proactive. Telemetry is collected and analyzed. Risk is assessed dynamically.
- Optimized: Automation and orchestration drive continuous improvement. Policies adapt in real-time, and the environment is resilient to breaches.
By mapping your current state to this journey, you can identify which areas of your Zero Trust program need attention and the next milestones.
Selecting the Right Model for Your Organization's Risk and Compliance Profile
There's no one-size-fits-all approach to Zero Trust. The right maturity model depends on your industry, risk tolerance, regulatory landscape, and business objectives.
- Regulated sectors like healthcare and finance may prefer models like NIST or CISA that offer prescriptive guidance and align with compliance mandates.
- Enterprises operating in multi-cloud or hybrid environments may lean toward Forrester's or Gartner's frameworks, which emphasize flexibility, automation, and telemetry.
- The pace of Innovation: Organizations undergoing digital transformation or operating in fast-moving industries (e.g., fintech, SaaS, healthtech) may benefit from Gartner's CARTA, which prioritizes agility and real-time risk adaptation.
- Organizations with limited resources should start with a simplified hybrid model and scaling maturity measurements over time.
The important thing is to choose your model with your business reality, not just your technical aspirations. Once you've selected a framework, you can build a scorecard that tracks maturity in terms of how effectively you're moving toward that target.
Operationalizing Zero Trust Measurement
Trust Scoring Systems
At the heart of Zero Trust is the principle of dynamic access control, granting or denying access not just based on static rules but on real-time assessments of Trust. This requires the ability to measure Trust continuously and adaptively, which is where trust scoring systems come into play.
Trust scores are not a single number but a composite view that reflects the behavior, compliance, and risk posture of users, devices, and workloads. When integrated effectively, these scores power the policy engines that drive enforcement in a Zero Trust architecture, deciding whether to grant access, prompt for re-authentication, or block activity altogether.
Building an effective Zero-Trust scorecard requires understanding how Trust is calculated and applied to the key entities in your environment.
User Trust Scoring
User trust scoring evaluates a user's risk and trustworthiness in real time. This is far more nuanced than traditional authentication models that simply check username and password.
Modern trust scoring for users incorporates:
- Authentication strength: Use of multi-factor authentication (MFA), biometric identity, or federated identity providers.
- Behavioral analytics: Unusual login times, impossible travel (e.g., logins from different geographies within minutes), abnormal access patterns.
- Contextual signals: Device type, geolocation, IP address, network reputation, and time-of-day analysis.
- Role and privilege: Admins and high-value targets often require stricter thresholds and lower tolerance for anomalies.
These inputs help generate a risk-adjusted trust score. If the score falls below a defined threshold, actions like step-up authentication, access denial, or session termination can be triggered automatically. This ensures access decisions are made based on current risk, not static roles or assumptions.
Example: A user logging in from an unmanaged device on a public Wi-Fi network outside of business hours, with no MFA, would receive a low trust score, potentially triggering step-up authentication or access denial.
Device Trust Scoring
Devices are often the entry point for attacks, especially in remote work, BYOD, and hybrid environments. Device trust scoring evaluates the security hygiene of endpoints in real-time.
Key elements include:
- Patch and Management: Whether the device has the latest security patches, OS version, and drivers.
- Endpoint protection: Integration with EDR/XDR platforms to detect threats, anomalies, or active compromises.
- Compliance posture: Presence of DLP (Data Loss Prevention) tools, disk encryption, firewall settings, and screen lock enforcement.
- Ownership status: Corporate-managed vs. personal device. Unmanaged or unknown devices are inherently higher risk.
Trust scores are calculated using endpoint telemetry and often integrated with device management tools (e.g., Mobile Device Management (MDM) / Unified Endpoint Management (UEM) platforms).
A high-trust device might be a corporate-managed laptop fully patched and enrolled in endpoint protection. In contrast, a personal, unmanaged device with outdated software would be a low-scoring device that may be restricted to limited resources or blocked altogether.
Workload Trust Scoring
In Zero Trust, workloads such as microservices, APIs, containers, and virtual machines must be treated as potentially compromised entities and must continuously verify each other's Trust.
Workload trust scoring takes into account the following:
- Application behavior: Based on baselines, are the processes, services, and API calls behaving as expected?
- API Telemetry: Does this workload usually talk to that database or API? If not, lateral movement may be occurring.
- East-West Controls: Is the container or virtual machine hardened? Are there vulnerabilities in critical packages or images?
- Environment signals: Is the workload in a production zone or a test environment? Is it exposed to the internet unnecessarily?
By assigning trust scores to workloads, organizations can detect anomalies early, contain compromised assets, and more effectively enforce micro-segmentation policies.
Integrating Trust Scores into Overall Security Posture
Trust scoring is most potent when it's not siloed. A unified Zero Trust architecture ingests scores from identity providers, endpoint telemetry, network analytics, and workload platforms to paint a composite risk picture.
Here's how this integration works:
- Trust scores feed into a policy engine (e.g., part of your Zero Trust Network Access or CASB platform).
- The engine makes real-time access decisions, such as granting access, stepping up authentication, or enforcing conditional access.
- Scores are continuously recalculated based on new telemetry or behavior. This allows adaptive policies that can revoke trust mid-session if risk increases.
- A central dashboard aggregates trust scores across users, devices, and workloads to give the security team a unified view of enterprise posture.
Trust scoring turns Zero Trust from a static model into a living system capable of learning, adapting, and responding to threats in real-time.
Mapping MITRE ATT&CK to Trust Validation
While trust scoring enables dynamic, context-aware decision-making, organizations also need a way to validate how well these decisions prevent or mitigate real-world attack behaviors.
This is where frameworks like MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) become essential. Organizations can bridge the gap between theoretical controls and practical defense by aligning trust scores with real-world adversary tactics, techniques, and procedures (TTPs). This mapping not only enhances detection and response but also sharpens the effectiveness of your Zero Trust implementation.
MITRE ATT&CK Framework
MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) is a curated knowledge base of cyberattack behaviors observed in real-world intrusions. It organizes attacker activity into tactics (goals) and techniques (how those goals are achieved) across multiple stages of the kill chain, from initial access to exfiltration.
Key aspects of the framework include:
- Tactics: The adversary's objectives (e.g., privilege escalation, lateral movement, command & control).
- Techniques & Sub-techniques: Specific methods (e.g., credential dumping, PowerShell abuse).
- Platform Coverage: Mapping applies across Windows, macOS, Linux, and cloud environments.
- Use Cases: Threat detection, red teaming, threat hunting, and now, increasingly Zero Trust enforcement.
By mapping telemetry and behavior data to ATT&CK techniques, organizations can build a behavioral trust model that reduces false positives and improves threat resolution speed.
Aligning Trust Scores with ATT&CK Techniques
Trust scoring systems can become exponentially more effective when linked with ATT&CK-based detections. Here's how that alignment works:
- User Behavior Mapping: If a user initiates a series of actions matching known ATT&CK techniques, such as unusual PowerShell commands (T1059.001), excessive file downloads (T1030), or access attempts to unusual systems, it lowers their trust score in real-time. These behavioral indicators are more context-rich than traditional policy violations and directly inform access control decisions.
- Device Behavior Mapping: Endpoints displaying indicators such as DLL injection (T1055), unexpected registry changes (T1112), or unauthorized privilege escalation attempts (T1068) would trigger alerts in the EDR/XDR layer. These findings feed directly into device trust scores, which can trigger containment policies like isolation from the network or downgrading access privileges.
- Workload/Service Behavior Mapping: When application workloads execute unauthorized scripts (e.g., T1059), initiate abnormal network flows (e.g., T1071), or access new APIs without justification, they may engage in lateral movement or internal reconnaissance. These behaviors lower workload trust scores and can be blocked via east-west traffic controls or API gateways.
- Network Telemetry Mapping: Observing encrypted command-and-control traffic (T1071.001), domain generation algorithms (T1568), or beaconing patterns can indicate a compromised device. The system can respond with step-up authentication, session termination, or segmented network access when correlated with identity and device scores.
By mapping behavioral indicators to MITRE ATT&CK, organizations connect trust decisions with adversarial insight rather than relying purely on static controls or threat signatures.
Main Use Cases for MITRE ATT&CK in Zero Trust
MITRE ATT&CK is more than just a threat reference, it's a strategic tool that brings adversary intelligence into Zero Trust decision-making. Organizations can enforce smarter, more responsive policies by aligning trust validation with known attack behaviors. Below are the key use cases where ATT&CK adds critical value to Zero Trust implementations.
Red Teaming and Adversary Emulation
Red teaming exercises test how well your Zero Trust defenses withstand realistic, targeted attacks. Security teams simulate advanced persistent threat (APT) behaviors using tactics, techniques, and procedures (TTPs) defined by ATT&CK.
Key outcomes:
- Reveal blind spots in detection, policy enforcement, and lateral movement containment.
- Validate Trust scoring logic by observing how simulated attacks impact user and device trust levels.
- Generate realistic, ATT&CK-aligned telemetry to tune behavioral analytics.
SOC Maturity and Detection Coverage
ATT&CK helps security operations centers (SOCs) map their capabilities against known attack methods, clearly showing where monitoring, response, and automation need improvement.
Key benefits:
- Identify gaps in telemetry and alerting
- Benchmark detection depth across identity, device, and network layers
- Align Zero Trust enforcement logic with evolving threat patterns
Insider Threat Detection
While Zero Trust aims to limit external threats, insider threats remain a significant risk. ATT&CK techniques such as credential abuse, lateral movement, or data staging provide the behavioral cues to detect risky insiders.
Use in Zero Trust:
- Enhances user trust scoring with identity-centric telemetry
- Flags abnormal behavior within "trusted" zones or accounts
- Enables real-time policy adaptation for insider risk scenarios
Penetration Testing and Security Control Validation
Penetration tests become more impactful when mapped to ATT&CK. Instead of only testing for vulnerabilities, teams validate whether their Zero Trust systems detect and respond appropriately to known techniques.
Strategic benefits:
- Measure tool effectiveness by mapping their detection and response capabilities to ATT&CK.
- Use the framework to design comprehensive pen tests covering multiple threat stages.
- Identify false negatives or gaps in policy coverage (e.g., missed privilege escalation attempts)
Breach and Attack Simulation (BAS)
BAS tools automate attack scenarios to assess how well controls perform in real time. When aligned with ATT&CK, they simulate actual adversary tactics that stress the Zero Trust fabric without introducing real risk.
Zero Trust impact:
- Measures how attack behavior affects user/device trust in-session
- Tests dynamic access enforcement against staged attacks
- Guides improvements in trust scoring models and access rules
Threat Intelligence Integration
Zero Trust thrives on context. ATT&CK maps known threat actor behaviors to specific techniques, helping organizations enrich their risk models and prioritize threats that matter most.
Use cases:
- Adjust trust thresholds for users/devices showing threat-aligned behavior
- Tailor responses to campaigns targeting your sector or assets
- Inform strategic decisions on control gaps and investment priorities
MITRE ATT&CK enables Zero Trust to be threat-informed, behavior-driven, and contextually adaptive. Whether used for detection, scoring, simulation, or policy enforcement, it transforms trust validation from static controls to dynamic security intelligence.
Dashboards and Automation Tools
As organizations embrace Zero Trust, the ability to visualize, automate, and act on trust metrics in real-time becomes critical. With so many moving parts, identities, devices, workloads, behaviors, organizations need intuitive, real-time ways to monitor trust decisions and enforce policy at scale.
Dashboards and automation tools form the operational core of a mature Zero Trust implementation. They allow security teams to see what matters, respond quickly, and communicate progress across the business.
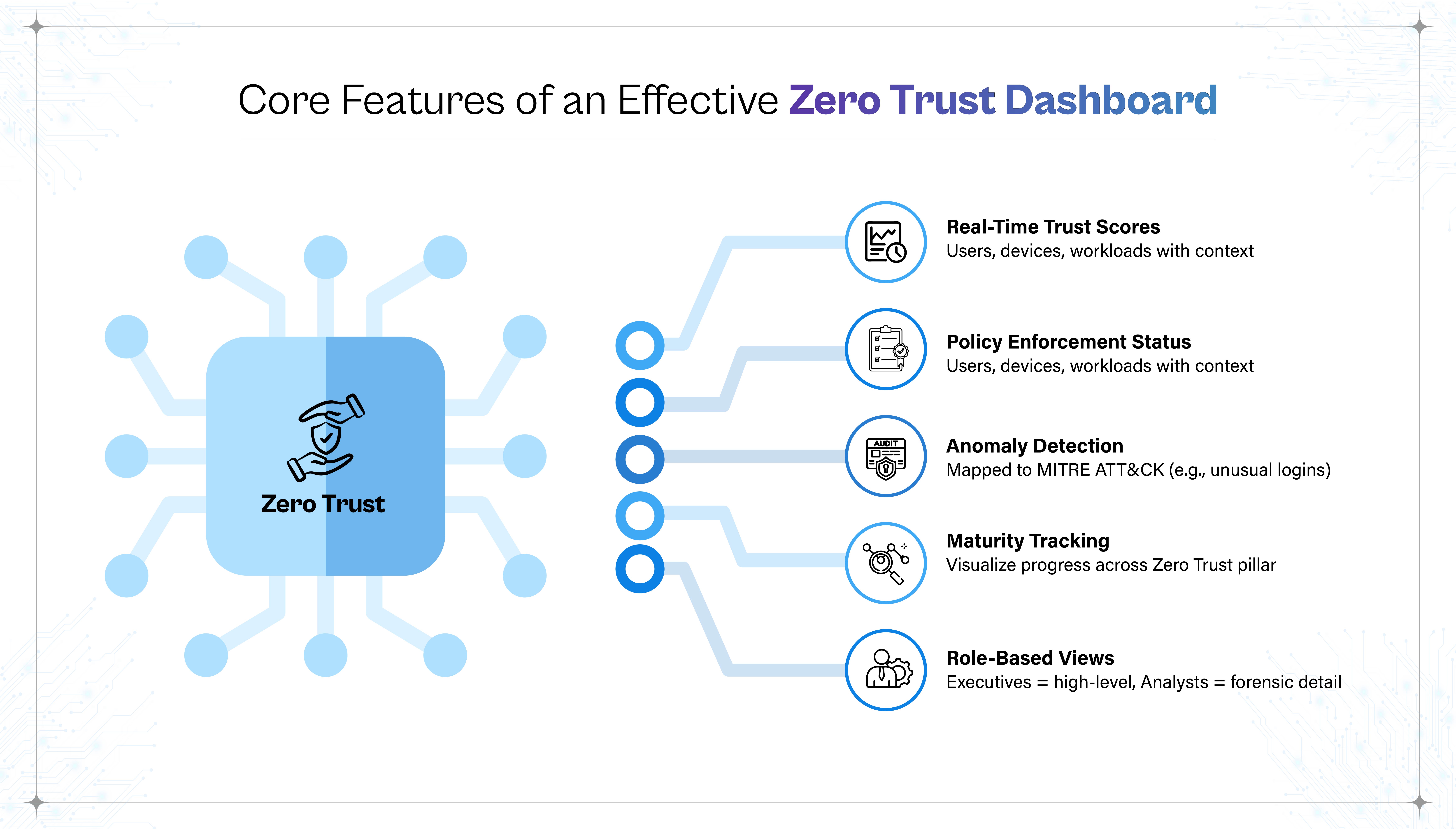
Core Features of Effective Zero-Trust Dashboards
An effective Zero Trust dashboard combines data from identity systems, endpoint tools, cloud services, and security platforms to create a unified view of your organization's security posture. It should answer not only what is happening but also why it matters and what should be done next.
Key features include:
- Real-time trust scores across users, devices, and workloads with contextual details.
- Policy Enforcement status: Track which policies are active when they were triggered, and what decisions were made
- Anomaly detection alerts mapped to MITRE ATT&CK techniques (e.g., unusual login attempts, privilege escalation).
- Maturity Model Tracking: Visualize progress across Zero Trust pillars (identity, device, network, workload, data).
These dashboards are often role-based. Executives need high-level risk insights and trends, while analysts require detailed forensic data to investigate and act.
Leveraging Automation for Real-Time Monitoring and Response
In a Zero-Trust model, speed is security. Threats evolve in seconds, so must your response. Automation tools bridge the gap between detection and enforcement, turning insight into action without manual intervention.
Automation use cases include:
- Trust score recalculation based on new telemetry (e.g., login location, device posture)
- Policy enforcement (e.g., revoking access, triggering MFA, isolating devices)
- Orchestration with SIEM, SOAR, and EDR tools for cross-platform response
- Auto-remediation of misconfigured accounts, vulnerable workloads, or unauthorized activity
Tools like SOAR platforms, ZTNA brokers, and risk engines take predefined thresholds and trigger workflows that contain risk before human analysts even step in.
Best Practices in Dashboard Design and User Experience
For dashboards to be truly impactful, they must be functional and user-friendly. Security teams often struggle with information overload. Hence, design matters. Here are some best practices to consider:
Best practices include:
- Use color-coded heatmaps and scorecards to highlight the urgency
- Provide custom filters and drill-downs for different teams (e.g., HR, IT, Finance)
- Include trend lines for KPIs like trust score drift, MFA coverage, and lateral movement attempts
- Display risk over time, not just events in isolation, this supports both real-time operations and executive reporting
Ultimately, a great dashboard doesn't just show data, it drives decisions. Dashboards and automation turn Zero Trust from theory into practice. They provide real-time insight, enable immediate response, and help you communicate progress and value to every stakeholder, from the SOC to the boardroom.
KPIs and KRIs for Measuring Zero Trust Success
In a zero-trust model, success isn't defined by the absence of breaches, it's measured by the ability to prevent, detect, and respond with precision.
Organizations need clear key performance indicators (KPIs) and key risk indicators (KRIs) to prove effectiveness and guide continuous improvement. These metrics turn your Zero Trust scorecard from a conceptual tool into a data-driven performance engine.

Understanding KPIs vs. KRIs
- KPIs (Key Performance Indicators) measure operational effectiveness. The answer to the question: How well are we doing?
- KRIs (Key Risk Indicators) measure exposure and threat levels. They answer: Where are we still vulnerable?
Both types of metrics are essential: KPIs drive accountability, and KRIs guide risk mitigation.
Example Metrics for Your Zero Trust Scorecard
Let's explore some actionable KPIs and KRIs that matter in a zero-trust context:
Key Performance Indicators (KPIs)
These metrics track how effectively your Zero Trust controls are being implemented, adopted, and enforced. They show progress and impact over time.
- Multi-factor authentication (MFA) Coverage Measures the percentage of users and systems protected by MFA. A higher number signals stronger identity assurance and reduced risk from credential theft.
- Trust Score Improvement Rate Tracks how trust scores improve for users, devices, and workloads. Improvements may result from software patching, behavioral baseline, or policy adherence.
- Policy Enforcement Success Rate: Percentage of access decisions correctly applied without overrides. Reflects the accuracy and efficiency of automated trust-based enforcement.
- Time to Contain an Incident Measures how quickly a threat is isolated or remediated after detection. Lower times indicate operational maturity and stronger response capabilities.
- Zero Trust Policy Adoption Tracks deployment progress across key domains, identity, devices, networks, workloads, and data, and reveals how broadly Zero Trust principles are being operationalized across the enterprise.
Key Risk Indicators (KRIs)
These metrics highlight where Trust is breaking down or increasing security exposure. They're essential for surfacing blind spots and prioritizing responses.
- Lateral Movement Attempts: Frequency of internal traffic patterns mimicking attacker techniques (e.g., credential hopping). Often, it is a red flag for compromised accounts or malware activity.
- Policy Override Frequency Counts how often manual exceptions are made to automated policies. High override rates may indicate usability issues, enforcement gaps, or policy misalignment.
- High-Risk Trust Scores: Percentage of users, devices, or workloads operating below your acceptable trust threshold. It helps identify assets that need remediation, quarantine, or review.
- Unpatched or Unmanaged Devices: These devices track endpoints without recent security updates or visibility through EDR/UEM tools, which often makes them soft targets for attackers.
- Anomalous Login Patterns include failed login spikes, unusual geographic access, or logins during non-standard hours. Behavioral deviations from baseline norms often signal account compromise.
- These metrics allow you to monitor not only whether controls are in place but also whether they're effective under pressure.
Real-Time vs Historical Trends: The Bigger Picture
Metrics are valuable when you can track them over time. One of the most powerful aspects of Zero Trust metrics is the ability to track progress over time. Metrics must reflect both current status and historical progress:
- Real-time metrics give you immediate visibility so that you can act fast, i.e., power dashboards, drive alerts, and trigger automation.
- Historical trends provide context for leadership, compliance reporting, and strategic planning.
By combining real-time data with long-term trends, your Zero Trust scorecard becomes more than just a snapshot. It becomes a strategic guidepost, helping you continuously improve and demonstrate meaningful progress to technical and executive stakeholders.
Reporting to Executives and Boards
One of the most common challenges in Zero Trust adoption isn't technical, it's communicative. While security teams work with telemetry, policies, and trust scores, executive leaders care about risk reduction, business continuity, and ROI. Bridging this gap requires more than raw data. It requires storytelling backed by metrics that resonate across both technical and non-technical audiences.
Tailoring Metrics for Technical and Non-Technical Audiences
Different stakeholders have different information needs. A board member isn't interested in the specifics of identity federation protocols they want to know whether the organization is safer today than it was last quarter.
To make Zero Trust metrics meaningful:
For technical teams (e.g., CISOs, SOC leads)
- They want details like the number of access attempts blocked, the number of high-risk devices isolated, and the shift in trust scores due to policy changes.
- Provide detailed insights into policy enforcement, incident trends, detection coverage, and trust score dynamics.
For executives and boards (e.g., board members, CFOs, business leaders)
- Focus on risk posture, maturity progress, and alignment with business goals. Use comparative indicators like "% reduction in high-risk users" or "time to contain threats."
Always ask: What decision is this metric enabling? If the answer isn't clear, reframe or replace it.
Telling a Story with Scorecards, Heatmaps, and Visualizations
Metrics are most persuasive when presented in clear, visual, and narrative form. Don't just share numbers, tell a story about progress, resilience, and preparedness.
Effective reporting tools include:
- Zero Trust maturity heatmaps: Visualize adoption across domains (identity, device, workload, data).
- Risk distribution graphs: Show how many users or assets fall into low-, medium-, or high-trust categories.
- Trend lines: Track the reduction of lateral movement attempts or time to respond to threats over months.
- Scorecards: Summarize KPIs and KRIs with green/yellow/red indicators to convey where attention is needed quickly.
These visuals transform operational complexity into business-aligned clarity.
Establishing a Reporting Cadence
Zero Trust isn't a one-time project, it's a continuous program. Your reporting should reflect that.
Recommended practices:
- Monthly operational reports: Shared with CISOs, IT, and security operations to guide day-to-day decision-making.
- Quarterly executive briefings: Present strategic insights to business leaders and boards aligned with risk appetite and investments.
- Annual Zero Trust assessments: Revisit maturity frameworks (e.g., CISA, NIST) to benchmark progress and refine long-term roadmaps.
This regular cadence reinforces Zero Trust as an ongoing commitment, not a "set and forget" initiative. It also ensures that security remains aligned with evolving business priorities.
Future Trends in Zero Trust Metrics
As cyber threats become more dynamic, Zero Trust metrics must evolve accordingly. The next generation of scorecards will go beyond traditional access controls and policy compliance to embrace behavioral intelligence, predictive risk modeling, and cloud-native visibility. Understanding where Zero Trust measurement is heading can help security leaders stay proactive, not just reactive.
Let's explore three key trends driving this evolution.
AI-Driven Behavioral Trust Scoring
Static thresholds and rule-based trust decisions are no longer enough. The future of Zero Trust lies in machine learning-powered behavioral analytics that continuously evaluate context, intent, and deviation from baseline norms.
What's emerging:
- AI models that assign dynamic trust scores based on real-time behavioral signals (e.g., unusual file access patterns, time-of-day anomalies).
- Continuous session risk scoring, where access isn't just granted at login but adjusted throughout the session.
- Integration with UEBA (User and Entity Behavior Analytics) to refine scoring models based on adaptive patterns.
This evolution enhances Zero Trust with real-time intelligence and risk-aware precision.
Integration with Cyber Risk Quantification Models (e.g., FAIR)
Boards demand quantifiable risk insights. Zero-trust metrics are starting to converge with financial risk models like FAIR (Factor Analysis of Information Risk) to help security leaders express their trust posture in economic terms.
Examples of integration:
- Assigning dollar values to trust breakdowns (e.g., the financial impact of a high-risk user operating outside policy).
- Linking maturity scores with risk exposure ranges to prioritize budget allocation.
- Using FAIR-aligned reporting to justify investments in Zero Trust tools or training programs.
This alignment bridges cybersecurity and business risk, fueling smarter decisions and tighter alignment with executive priorities.
Metrics for Hybrid and Multi-Cloud Zero Trust Strategies
As more organizations operate across AWS, Azure, and Google Cloud, Zero Trust metrics must become cloud-native and platform-agnostic.
Future focus areas:
- API trust scoring: Evaluating cloud-native workloads' behavior, security posture, and communication patterns.
- Cross-cloud trust telemetry: Correlating trust signals across environments to maintain consistent policy enforcement.
- SaaS app compliance mapping: Measuring how third-party apps align with Zero Trust principles, such as strong identity controls and tenant isolation.
The future of Zero Trust metrics is intelligent, contextual, and business-aligned. From AI-driven scoring to cross-cloud posture tracking, measurement is no longer about static compliance, it's about dynamic risk navigation. Security teams that embrace these trends will gain a competitive edge in resilience, agility, and executive Trust.
Conclusion: Building a Culture of Measurable Trust
Zero Trust is not a toolset, it's a mindset. And like any strategic mindset, it only drives change when progress is measured, risk is understood, and insights are shared across the organization.
A well-structured Zero Trust scorecard is more than a reporting mechanism, it's a mirror of your security maturity. It reflects not just how many controls you've deployed but how confidently you can say: our users are verified, our systems are resilient, and our business is protected.
Security leaders must move beyond vague notions of "zero trust readiness" and embrace data-driven validation. Whether you're starting with MFA metrics or layering in real-time behavioral trust scores and MITRE ATT&CK correlations, the goal is the same: make Trust observable, contextual, and actionable.
The future of cybersecurity belongs to organizations that treat Zero Trust not as an initiative, but as an operating system for resilience. And the scorecard is your user interface.
Use it not just to monitor your defenses but to lead with confidence, justify every investment, and continuously earn Trust across every layer of your business.
Advance Zero Trust with Cogent Infotech
Stop guessing and start measuring. Cogent Infotech architects end-to-end Zero Trust programs that convert philosophy into quantifiable results. We:
- Design custom scorecards aligned to NIST, CISA, and Forrester models
- Build AI-driven trust-scoring engines for users, devices, and workloads
- Integrate MITRE ATT&CK mapping, real-time telemetry, and automated enforcement
- Deliver executive dashboards that translate security posture into business ROI
Ready to make measurable trust your competitive edge? Let’s connect and elevate your Zero Trust maturity.







%402x.svg)

.jpg)

.jpg)


