Cybersecurity in an AI World: Embedding Security by Design for Resilience in 2025



AI is no longer an experiment. In 2025, it sits at the heart of how individuals and enterprises innovate, operate, and compete. It has evolved from powering isolated use cases to becoming embedded in how businesses operate, informing decisions, automating operations, and even interacting directly with customers. For many enterprises, AI is now a strategic advantage.
But while adoption is accelerating, security is not.
As AI scales, so do its vulnerabilities. Most systems are being deployed faster than they’re being secured. And the consequences are becoming clear: unpredictable model behavior, exposed pipelines, and attackers leveraging AI to scale and sharpen their threats.
'This is no longer just an IT challenge, it’s a business risk.'
According to Accenture’s 2025 Technology Vision, 70% of global leaders say their AI adoption has outpaced their ability to secure it. Yet, these AI systems are increasingly controlling access to sensitive data, informing high-stakes decisions, and interfacing with users at scale.
This gap of protection is no longer a technical oversight, it’s a strategic vulnerability. Threat actors are exploiting it with AI-augmented attacks: poisoning training data, reverse-engineering proprietary models, and deploying deepfakes that erode brand trust and spread misinformation at scale.
The core issue? Most organizations still treat AI as software, not as a dynamic, adaptive system that requires its security architecture.
Traditional defenses are failing to detect novel AI-specific threats. Traditional cybersecurity was built around fixed perimeters, known assets, and predictable behavior. AI brings none of that. The models are opaque. The data is dynamic. The systems are constantly learning and adapting. And when something goes wrong, a poisoned dataset, a biased model, a manipulated outcome, the damage is hard to detect and even harder to contain.
AI doesn’t break in familiar ways. It learns, evolves, and scales. Which means the way we secure it must evolve too. That’s why security by design has become a core leadership issue.
It’s not about adding controls after deployment, it’s about building trustworthy, resilient, and compliant AI systems from the ground up. Embedding cybersecurity across the full AI lifecycle, from data ingestion and training to deployment and monitoring, doesn’t slow innovation. Done right, it accelerates it, with greater confidence, clarity, and control.
This is a guide for leaders who are shaping the future of their business with AI. It explores how organizations can embed security into the DNA of their AI strategies.
In this, we’ll explore how enterprise leaders can:
- Navigate the evolving AI threat landscape, and identify where traditional defenses are falling short
- Embed security by design across the AI lifecycle, from data pipelines to model deployment
- Align AI security with governance and regulatory expectations, including NIST and global frameworks
- Turn resilience into a strategic advantage, enabling faster, safer, and more trusted innovation
Because in 2025, resilience isn’t just about surviving cyberattacks. It’s about protecting the systems that will define your next chapter of innovation.
The Expanding AI Attack Surface
AI is fundamentally changing how businesses operate, but it’s also redefining how businesses are attacked.
The more deeply AI becomes embedded across workflows, decisions, and customer touchpoints, the more it reshapes the enterprise threat surface. Not with theoretical risks, but with real-world exposure. Every layer from raw data ingestion and third-party models to API deployment and inference adds a new set of vulnerabilities.
This isn’t about future threats. This is about the vulnerabilities that are already here, and growing faster than most organizations are prepared to handle.
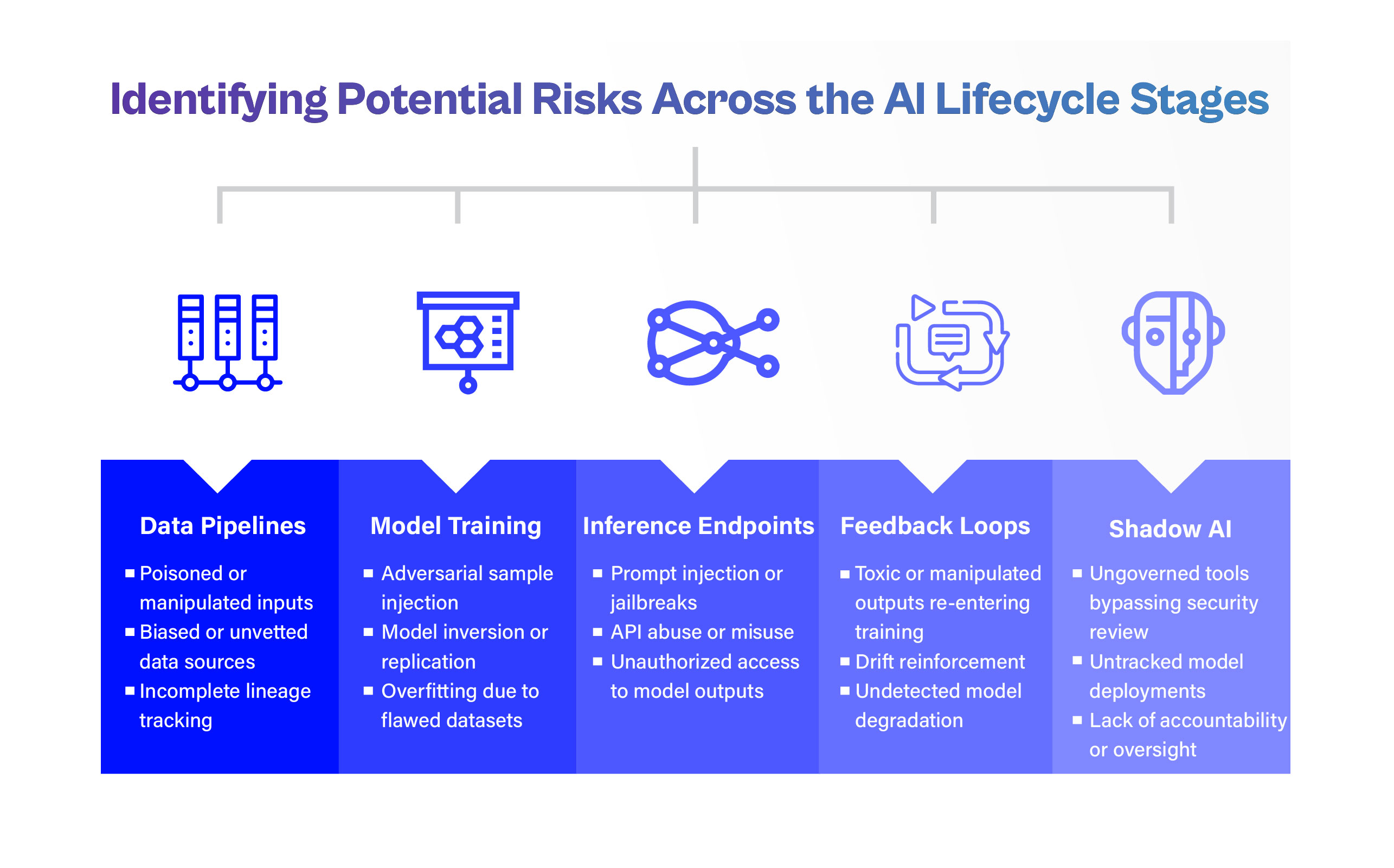
AI Adoption Driving New Vulnerabilities
What was once experimental is now business-critical. In the rush to harness AI’s transformative potential, many organizations are building faster than they’re securing. But here’s the challenge: AI is being deployed into production environments that were never designed with these systems in mind.
The result? A rapidly growing set of vulnerabilities hiding in plain sight. The three risk areas stand out:
- Manipulated Inputs: Techniques like data poisoning and prompt injection are being used to distort training, manipulate outputs, or cause system failure. This undermine model performance and trust.
- Exploitable Outputs: AI systems don’t just take in data, they generate it. Without proper safeguards, can disclose confidential information, deliver harmful content, or propagate errors downstream.
- Exposed Access Points: As AI services are exposed via public and internal APIs, many lack hardened authentication, or monitoring, making them ripe for extraction, abuse, or denial-of-service attacks.
And then, the growing problem of Shadow AI, business units adopting AI tools without oversight or governance. These tools often bypass formal security review, creating blind spots for enterprise risk teams. According to reports from Accenture says, shadow AI use is an emerging breach vector in enterprise environments.
AI Pipelines Are Complex and That Complexity Obscures Risk
AI systems are not plug-and-play. They’re built on multi-stage pipelines involving external data sources, proprietary models, open-source frameworks, cloud services, and operational APIs. And these aren’t managed by a single team, they span product, data science, engineering, and operations.
Each phase of the AI lifecycle introduces a unique set of vulnerabilities:
- Data pipelines may ingest unverified or poisoned data from public or third-party sources.
- Model training environments often lack sufficient access controls or logging.
- Deployment pipelines may use open-source components that aren't properly vetted.
- Monitoring systems may not flag dangerous drift or unexpected behavior.
Security is failing because visibility is fragmented and accountability is unclear.
This lack of transparency makes it hard to detect when something goes wrong, or when an attacker makes it go wrong on purpose.
As enterprises rely more on open-source tools, they’re creating a new kind of digital supply chain, one where risks can be introduced at any point and spread without being noticed. According to IBM’s Threat Intelligence Index, nearly 31% of AI-related breaches trace back to supply chain or third-party pipeline vulnerabilities.
Traditional Defenses Are Not Designed for Adaptive Systems
Most security architectures today were built to protect code, endpoints, networks, and access. But AI systems are none of those things. They are:
- Adaptive, not static
- Data-driven, not rule-based
- Probabilistic, not deterministic
Thus, Key gaps include:
- Perimeter-Based Thinking: AI systems run across cloud-native environments, edge devices, and external APIs, well beyond the protection of conventional perimeters.
- SIEM Blind Spots: Security monitoring platforms often can’t track model-specific indicators, such as performance drift, bias emergence, or unauthorized retraining events.
- IAM Limitations: Role-based access systems lack the granularity to manage permissions for specific datasets, models, inference endpoints, or training tasks.
Gartner projects that by 2026, 30% of AI models in production will be intentionally manipulated by adversaries through indirect attacks, including data tampering, pipeline poisoning, and model theft.
The result? Security is strongest everywhere but where AI lives.
What Is ‘Security by Design’ in AI?
In today’s AI-first enterprise, cybersecurity can no longer wait until the end of development. Traditional approaches, patching vulnerabilities post-deployment or reacting to incidents after damage is done, are no match for intelligent systems that learn, evolve, and operate at scale.
Security by Design means rethinking AI development and applying AI risk management principles from the ground up.It’s not just a best practice, it’s a mindset: one that embeds protection, trust, and resilience into every phase of the AI lifecycle, from data ingestion and training to deployment and monitoring.
This shift is not just about avoiding risk, it’s about enabling innovation at scale with confidence. In a world where AI now powers decisions that affect customers, operations, and strategy. Security is not a cost center. It's a business enabler.
Building Secure AI from Architecture to Deployment
Security by Design starts at the foundation, the architecture. Instead of bolting on controls after launch, leading enterprises are designing AI systems with guardrails from day one.
Key principles include:
- Securing data pipelines with verification, encryption, and traceability built into ingestion and transformation stages.
- Protecting model training through clean, validated datasets, environments, and access controls that prevent data poisoning or unauthorized manipulation.
- Designing for runtime safety, including behavioral baselines, anomaly detection, and rollback mechanisms that activate when something goes wrong.
High-performing enterprises (Accenture, 2025) are implementing “security gates” between AI lifecycle phases, checkpoints that stop vulnerable models from progressing without validation, explainability, or compliance sign-off.
Embedding Controls Across the AI Lifecycle
Security by Design isn’t just an IT problem. It must be operationalized across every team involved in building and deploying AI, from data scientists and DevOps to product managers and compliance officers.
Here’s how that looks in practice:
- Input Validation: Catch bad data before it hits the model. Use filters, anomaly detectors, and adversarial testing to protect training and inference stages.
- Role-Based Access Controls: Apply Zero Trust principles to who can access models, APIs, datasets, and retraining triggers, down to the function level.
- Model Governance: Track model lineage, who trained what, when, with which data, and how it performs in the wild.
- Full Auditability: Every model decision should be traceable. Logging should include versioning, usage patterns, output behavior, and alert flags.
NIST’s AI Risk Management Framework (2023) stresses continuous risk monitoring and lifecycle controls, not one-time audits as critical to building resilient systems.
Insights from Accenture’s 2025 Findings
AI is no longer only enhancing business operations; it's becoming a business. But there's a problem: while enterprises are scaling AI faster than ever, their ability to secure it isn’t keeping pace.
This isn’t a distant concern. It’s playing out in real time, and it’s a strategic vulnerability.
The Numbers Tell a Clear Story / The Resilience Gap Is Widening
Accenture’s Technology Vision 2025 reports this imbalance perfectly...
“AI adoption is outpacing AI security maturity.” Accenture Technology Vision 2025
- 70% of executives say their AI deployment is moving faster than their security strategy.
- 77% have weak or fragmented security controls around AI pipelines.
- Only 13% have advanced cyber capabilities to secure adaptive systems.
- 90% admit they’re not prepared for AI-driven threats.
These aren’t marginal oversights, they’re signals of a widening resilience gap. As AI takes on more business-critical roles, every ungoverned dataset, unmonitored model, or exposed API becomes a potential breach point.
From Insight to Action: The Leadership Imperative
The message from Accenture is clear: securing AI cannot be reactive or siloed. It’s not only an IT issue, it’s a boardroom issue. Security by design must become an enterprise-wide priority, woven into architecture, governance, and culture.
Key Recommendations:
- Move from reactive patching to AI-specific threat modeling
- Adopt Zero Trust across data, models, APIs, and users
- Invest in explainability, auditing, and lifecycle observability
- Build cyber capabilities that evolve alongside your AI stack
Strategic Takeaway: In an AI-first world, trust isn’t earned by innovation alone, it’s earned by securing that innovation at every step. The organizations that get this right won’t just avoid breaches. They’ll accelerate safely, gain market trust, and define what good looks like in the next chapter of digital leadership.
The Role of Zero Trust, Auditing, and Model Management
Securing AI isn’t about patching around the edges, it’s about rethinking core assumptions. As AI systems gain autonomy and hold decision-making, traditional defenses — VPNs, firewalls, endpoint tools, no longer provide sufficient coverage.
What’s needed is a layered, modern architecture built for the dynamic and distributed nature of AI. And the three capabilities that stand out are : Zero Trust, Auditing, and Model Management.
Zero Trust: Treat Every Interaction as a Potential Breach
Zero Trust changes the game by enforcing the principle of “never trust, always verify.” In the context of AI, this means:
- Authenticating every data access request, from training to inference
- Applying granular, role-based controls over who can modify, retrain, or deploy a model
- Monitoring for anomalies in model behavior, access patterns, and data usage
- Isolating critical systems to prevent lateral movement if a breach occurs
Gartner forecasts that by 2025, 60% of enterprises will replace VPNs with Zero Trust Network Access (ZTNA). For AI, this means moving beyond perimeter defense , and securing the core.
Auditing and Observability: Visibility Is the New Perimeter
You can’t secure what you can’t see. The "black box" nature of AI models makes traditional monitoring insufficient. That’s why auditing and logging are now mission-critical.
Leading enterprises install full-stack observability across the AI lifecycle:
- Log model training events: who trained what, on which data, with which hyperparameters
- Track inference requests and response patterns for anomalies or abuse
- Track data inputs for shifts, poisoning attempts, or regulatory violations
- Maintain change histories for every model version and deployment
According to IBM’s 2025 Threat Intelligence Index, enterprises with strong AI audit trails respond 35% faster to incidents. Auditing is no longer a compliance checkbox , it's how leaders establish trust, accountability, and forensic readiness.
Model Management: Govern AI Like Software + Infrastructure
AI systems aren’t static codebases, they’re adaptive, probabilistic, and often unpredictable. Managing them requires discipline, tooling, and clear ownership. Enter ModelOps or MLOps, platforms that bring DevSecOps principles to the AI stack.
Key capabilities include:
- Versioning: Maintain full lineage across models, datasets, and outputs
- Automated testing: Validate robustness against adversarial inputs before deployment
- Real-time monitoring: Detect model drift, accuracy drops, or toxic outputs
- Access control: Restrict who can deploy, retrain, or rollback a model
- Policy enforcement: Trigger auto-rollbacks if performance or risk thresholds are breached
Capgemini reports that scalable, secure AI in 2025 will depend on ModelOps platforms deeply integrated with security tooling. Futuristic organizations now hold “AI Change Board” reviews, mirroring software release practices, where security, legal, and business teams sign off before models go live.
From Tools to Trust: Building a Resilient AI Architecture
AI resilience isn’t about achieving perfect protection, it’s about building systems that can detect, contain, and recover from failure fast. That requires:
- Granular IAM for AI assets
- Lifecycle checkpoints across training, deployment, and retraining
- Behavioral baselines for inference anomalies
- Automated alerts for hallucinations, bias, or data misuse
Resilient AI is not just a security achievement, it’s a trust asset.
Best Practices for Building Cyber-Resilient AI
AI systems are dynamic, high-impact assets, not static code. They learn, adapt, and operate autonomously in live environments. That’s why cybersecurity for AI must move beyond checklists and bolt-ons. It requires intentional design, embedded controls, and cross-functional accountability. Thus, embedding cybersecurity as a first principle across architecture, governance, and team.
Below are four foundational practices that define cyber-resilient AI leaders.
Risk Assessments and Threat Modeling for AI Pipelines
Traditional security scans can’t keep pace with AI’s complexity. That’s why high-performing enterprises now conduct AI-specific threat modeling before development begins. Organizations that integrate AI threat modeling reduce incident remediation time by up to 45% (Accenture, 2025).
Pro Tip: Use frameworks like MITRE ATLAS and the NIST AI RMF to simulate threats and design safeguards early.
Strengthen IAM for Models, Data, and Pipelines
AI systems operate across environments: cloud, hybrid, and edge, often interacting with sensitive data, user inputs, and proprietary logic. Poor access control isn’t just a misstep; it’s an open door to attackers. This makes identity and access management (IAM) more important
AI-resilient IAM strategies include:
- Least privilege access for model training, tuning, and deployment
- Role-Based Access Control (RBAC) across ML pipelines and APIs
- Federated identity and MFA for every user, model, and system
- Secrets management for keys, tokens, and credentials tied to AI assets
- Model identity: treating models as operational entities with their own access credentials and audit trails
Pro Tip: Treat models and pipelines as digital identities. They should have their own credentials, entitlements, and telemetry.
Explainability, Traceability, and Governance
If you can’t explain how your AI system made a decision, you can’t defend it, or regulate it.
Resilient AI systems are auditable and interpretable by design:
- Explainable AI (XAI): Translate predictions into human-understandable rationale
- Model traceability: Link outputs to specific model versions, data inputs, and configurations
- Auditability: Capture every step from training to tuning to deployment
- Governance frameworks: Review models for fairness, safety, and compliance before release
Key Takeaway: Explainability isn’t a technical bonus, it’s a boardroom concern. It enables accountability, simplifies regulatory response, and protects brand trust.
Cross-Functional Collaboration
Siloed security doesn’t scale in an AI-first organization. Resilience demands tight collaboration between cybersecurity, data science, engineering, compliance, and product teams. Also, Accenture’s 2025 report shows 74% of cyber-resilient firms formally align AI and cybersecurity teams.
What high-performing teams do:
- Embed security architects in AI development teams
- Run cross-functional threat modeling workshops in early stages
- Create shared dashboards for monitoring AI performance and anomalies
- Establish AI Change Review Boards to check model risk pre-deployment
- Align on shared KPIs across security, MLOps, and business stakeholders
The Business Case for AI Security
Secure AI isn’t just about protection. It's about the security of those systems, which becomes essential for trust, innovation. It’s also about building the confidence to scale responsibly, move faster, and lead in an increasingly regulated, risk-sensitive digital economy.
Compliance, Trust, and Breach Recovery
AI systems operate at the intersection of autonomy, data sensitivity, and high-stakes decision-making. As global regulations evolve, from the EU AI Act to NIST’s AI RMF , compliance and auditability are no longer optional.
Organizations need systems that are explainable, observable, and defensible
Strategic Value of Secure-by-Design AI
- Regulatory Compliance - Avoid costly rework and fines by embedding policy-aligned controls early
- Customer Trust - Demonstrate explainability, fairness, and secure handling of data
- Incident Response - Traceable logs accelerate root cause analysis and breach containment
- Reputational Risk -Show leadership in responsible AI and avoid public fallout from security failures
Faster Innovation with Less Risk
Contrary to traditional thinking, security doesn’t slow innovation, it enables it. Secure-by-design AI:
- Reduces the cost and time of post-deployment fixes
- Speeds up compliance approvals
- Builds confidence among boards, regulators, and users
Accenture’s Technology Vision 2025 finds that companies integrating AI and cybersecurity from day one experience:
- Up to 34% faster time-to-value on AI initiatives
- Fewer delays from regulatory pushback
- Better model reusability and governance at scale
Security, when embedded into the development pipeline, becomes a catalyst, not a constraint, for agile, trustworthy innovation.
Security as a Strategic Differentiator
In a world where trust is a brand asset, cybersecurity in AI becomes a lever for growth. According to Gartner, organizations with mature AI governance will outpace competitors in responsible innovation by 50% by 2026.
A robust security posture:
- Reduces rework from vulnerabilities
- Simplifies compliance with audit-ready frameworks
- Speeds executive approvals for new AI launches
- Enables model portability across teams or cloud environments
- Builds stakeholder trust across the ecosystem
Secure AI builds ecosystem confidence, enabling partnerships, market leadership, and sustained growth.
Conclusion: Security by Design Is the Foundation of Resilient AI
The pace of AI adoption is accelerating, but so are its vulnerabilities. As AI systems become core to business strategy, infrastructure, and customer experience, they also become high-value targets in an evolving threat landscape. Traditional security models weren’t built for this. Patchwork protections and reactive fixes simply won’t hold up.
The organizations that will lead in 2025 and beyond are those that treat AI security as a first principle, not a final checkpoint.
Embedding security by design means building AI systems that are robust from the inside out: governed, explainable, accountable, and resilient at every layer. It’s not just about compliance. It’s about trust, continuity, and competitive strength in an AI-driven economy.
Cybersecurity is no longer a cost of doing business, it’s a catalyst for scaling AI with confidence. It clears the runway for innovation. It earns the trust of regulators, partners, and users. And it transforms risk into resilience.
AI security is not just about preventing loss. It’s about enabling what’s next. It protects what matters today, and powers what’s possible tomorrow. For enterprises betting big on AI, resilience is the new ROI.
In 2025, resilience is not reactive. It’s designed in from day one. Futuristic leaders are building AI systems that are not only high-performing but also compliant, trustworthy, and defensible.
Your Next Step: Explore Our AI Governance Services
Ensure your AI initiatives align with regulatory frameworks, mitigate risk at scale, and accelerate innovation, all while earning the trust of customers, partners, and boards.
Talk to our Cybersecurity Expert – Get tailored guidance for your enterprise AI landscape.







%402x.svg)



.jpg)


